“Publicity is justly commended as a remedy for social and industrial diseases. Sunlight is said to be the best of disinfectants; electric light the most efficient policeman.”
–Louis D. BrandeisFootnote 1
How does the publicity of noncompliance affect international order? Brandeis's sunshine analogy invokes an intuitive and widely shared answer: revealing infractions can strengthen socio-political rules. This positive association between the exposure of violations and a well-regulated political system is manifested in several influential areas of international relations scholarship. Rational institutionalist theories, along with research on norms and international law, have argued that publicizing noncompliance can reverse deviant behavior through punishment and sanctions, and can reassure compliers that they will learn whether others fail to comply.Footnote 2 Indeed, many international organizations that monitor state compliance reflect this logic because they are designed to facilitate the identification and publicity of transgressions.Footnote 3
Despite this intuitive logic, theoretical and empirical studies in sociology, criminology, and economics suggest that the relationship between visible rule breaking and social order is more complex. Decades ago, social theorists noted that the opacity of violations of social norms allows many implicit and explicit rules to persist.Footnote 4 More recently, studies of compliance with laws about everything from alcohol consumption to tax reporting have found that increased transparency about the rate of noncompliance can increase individuals' propensities to break these regulations.Footnote 5
This raises two puzzles for scholars of international politics. First, when might the disclosure of international rule violations strengthen regimes, and when might it endanger them? Answering this question requires first identifying the mechanisms through which the revelation of noncompliance affects regime health. Second, how do rule enforcers react to noncompliance in light of these concerns? Well-informed states that detect noncompliance can influence whether the international community learns about deviant behavior. Such states should strategically manipulate the provision of information about violations of international laws in light of the likely impact of publicity.
In this article we develop and test a theory that answers these questions, arguing that while the conventional wisdom often holds, it breaks down under key circumstances that are prevalent in international settings. We develop two mechanisms by which exposing rule violations endangers norms and formalized legal regimes: (1) when a state learns of high levels of noncompliance in the international community, the perceived social opprobrium from that state violating the norm is reduced (the pessimism mechanism), and (2) when a state learns of specific instances of noncompliance that may pose a direct threat to the state's security, it may seek to defend itself (the threat mechanism). Next we analyze how these mechanisms inform the strategic behavior of a well-informed state with enforcement capabilities, modeling the conditions under which such a state intentionally hides another state's rule violations to protect the regime. When the well-informed state finds it difficult to reverse a case of noncompliance, publicity can encourage additional instances of rule abandonment, leading regime advocates to strategically withhold information to perpetuate the practical and legal ambiguity about a given infraction. Otherwise, such a state will publicize noncompliance in line with the conventional view.
We evaluate the theory's observable implications in the nuclear nonproliferation setting, focusing on whether decision makers in the regime's strongest advocate, the United States, intuitively grasped the appeals and dangers of revealing violations. Drawing on recently declassified internal documents, we find that US leaders strategically obfuscated violations of the nuclear regime when they believed that a state's nuclear progress was irreversible and would lead to other states' noncompliance. Otherwise, US leaders shared their information with other states to reassure such states and to organize punishment of the violator, mirroring the conventional wisdom. The nuclear domain illustrates potential downsides of this pattern of behavior for the regime as a whole: high rates of concealment can undermine confidence in the enforcement of the regime.
Our focus on how strategic actors react to nuclear proliferation allows us to shed light on an empirical puzzle: Why would a regime advocate withhold its information about another state's nuclear program, especially given extant theory about the benefits of revelation? While obfuscating a state's own nuclear ambitions is sensible, the strategic purpose of hiding other states' programs is less clear. Beyond the nuclear realm, the article re-examines and revises the common assumption of scholarship on both international norms and international organizations that knowledge improves compliance with rules and norms. We combine game-theoretic tools, social-theoretic insights from outside of political science, and archival documentary evidence to show that this view is incomplete. Under some conditions, shining a spotlight on rule violations increases the stress on a regime, resulting in the strategic withholding of intelligence. By addressing these large theoretical debates, our findings also speak to treaty violations and enforcement efforts in other arenas including ceasefire agreements, global trade rules, and environmental accords.
The Spotlight's Benefits
A common theme of studies of both norms and international regimes is that widely shared knowledge about noncompliance helps to maintain a rule-based international order. A monitor's standard role is to facilitate cooperation when states mistrust each other, which occurs when they remain uncertain about whether their partner prefers to respond to cooperation with cooperation or defection.Footnote 6 A monitor can allow cooperation to emerge when both parties are too mistrustful to do so otherwise by reassuring each that the other side wants to cooperate.Footnote 7 A variety of studies echo this positive view of monitoring. For example, constructivist models of norm evolution argue that drawing attention to norm-inconsistent behavior can stimulate domestic and international pressure and sanctions, which can force deviant states to enter or rejoin normative regimes.Footnote 8 Recent applied studies have systematically assessed this intuition by analyzing how publicity affects compliance with international human rights norms,Footnote 9 typically finding that condemnation motivates the target state to comply.Footnote 10
Also germane to our theory is the larger literature on cooperation and international institutions. Beginning with Keohane, rational institutionalists have argued that cooperation is often difficult because states fear being suckered into complying while their partner violates the agreement.Footnote 11 International institutions and other monitors, however, can facilitate cooperation by easing access to information about states' adherence to the rules. This can reassure states that they will not be taken advantage of because they will learn of defections.Footnote 12 By providing such information, international organizations (IOs) can encourage reciprocity, solve political hold-up problems, allow states to develop reputations for compliance, and coordinate punishments for defection.Footnote 13 While the degree of centralized monitoring varies,Footnote 14 a common assumption is that exposing noncompliance strengthens regimes.
The Spotlight's Dangers
Despite the widespread positive view of transparent monitoring, a countercurrent of research on the possible dangers of information revelation in global governance hints at a more complex story. For example, some studies suggest that greater domestic institutional transparency provides information that sharpens value conflicts among groups, empowers dangerous nongovernmental actors, and breeds misperception of intentions during crises.Footnote 15 Others highlight the downsides of revealing diplomatic negotiations regarding international agreements, a step prior to the compliance stage on which we focus.Footnote 16 Most relevant to our argument is Lindley's finding that information gleaned from institutionalized monitoring can be counterproductive because it can facilitate coercive diplomacy.Footnote 17
We build on these ideas by arguing that when states are willing to cooperate with each other without additional information about each other's willingness to respond to cooperation with more cooperation, monitoring can actually prevent cooperation by publicizing defections, leading the other party to defect as well. This can occur through the pessimism and threat mechanisms, where the first is triggered when high levels of noncompliance reduce the perceived social opprobrium from violating the norm, and the second is activated when specific violations that pose a direct threat lead a state to defend itself by defecting. To make our argument, we adapt related theoretical and empirical findings from outside of political science to the context of states in an anarchic international system.
The first mechanism builds from mid-century social-theoretic analyses of privacy and deviance, which argue that ignorance and concealment can create the appearance that a normative consensus exists when in fact it may not. Actors may then comply as a result of a mistaken belief that if they do not, they will face ridicule or stigma. Hiding transgressions is thus not only attractive for the rule violators but is also “an important functional requirement for the effective operation of social structure”Footnote 18 because it “reinforc[es] the assumption that deviation from the rules is statistically insignificant.”Footnote 19 Influential sociologists like Erving Goffman, Georg Simmel, and others thus noted the stabilizing effects of masking devianceFootnote 20 because the higher rates of perceived compliance strengthen the social bonds and shared commitment to the rules.Footnote 21 In contrast, if actors discovered that many others violated the rules, they would conclude that following the norm was less highly valued than they had previously thought, and that straying from it would trigger less severe reputational consequences. This theme also appears in more recent work. In diverse settings from juvenile gangs to tax compliance, sociologists and economists have found that hard-to-observe transgressions lead actors to underestimate the rate at which such violations occur, reinforcing the economic incentives and perceived social pressures for others to remain in compliance with the rules.Footnote 22
These studies point to an overlooked effect of publicizing rule violations in the international realm: publicity can eliminate ignorance and uncertainty about defections, relaxing the strategic incentives and normative pressure to remain within a regime. As states become aware of other states' violations—regardless of the direct threat that the violations pose—the behavioral and ideational consensus in the international community may weaken, which can alter states' assessments of the benefits associated with their own cooperation. States may realize that their reputations will not be tarnished from breaking the rules to the degree that they once believed. The increasing pessimism about the overall rate of compliance can thus lead to second-order or reactive violations.Footnote 23
A second and distinct effect of publicizing rule violations—which is especially relevant to the anarchic international system—is a sharpening of the threat that these violations pose to other states. This scenario is most plausible in regimes that govern interdependent state activities where economic, military, or other advantages are generated by defections from norms.Footnote 24 Because a rule violation can create negative consequences for other states, the publicity of noncompliance can alert states to the threat and thereby lead to reactive violations. Unlike the pessimism mechanism, which results when any state violates a given norm, this mechanism comes into play when a violation poses a direct danger. For example, in the nuclear realm, the acquisition of weapons by nearby or enemy states can have particularly severe consequences.Footnote 25 These second-order rule violations, in turn, can accumulate and generate a wider unraveling of participation in a regime.Footnote 26
Many states recognize these dangers of transparent monitoring, and thus often seek to limit knowledge of violations.Footnote 27 When an enforcer is not “exploitation averse”—that is, when it prefers a single defection to mutual defection—it has an incentive to hide the original defection to prevent additional violations from occurring.Footnote 28 Our theory thus expects states with unique information about violations that support the goals of the regime to carefully manage the publicity of violations when the dangers we highlight are present.
Signaling and Strategic Obfuscation
We develop a formal model to generate testable empirical hypotheses about how enforcers strategically manage information in light of the countervailing effects of publicity that we identify. The game is referenced but, because of space constraints, the formalization appears in the supplementary appendix. The central actors are three states: a regime monitor and enforcer (E), state A, and state B, where B represents a member of the international community. Prior to the start of the game, neither A nor B have broken the law. The game begins with Nature randomly drawing A's benefit from a violation so that A derives a large benefit (![]() $\overline b $) with probability 1 − p and a small benefit (
$\overline b $) with probability 1 − p and a small benefit (![]() $\underline b $) with probability p, where
$\underline b $) with probability p, where ![]() $\overline b \gt \underline b $.Footnote 29 A then chooses whether to violate the rules (v A) or not (¬v A). B does not observe A's action while E does because of E's informational advantage.
$\overline b \gt \underline b $.Footnote 29 A then chooses whether to violate the rules (v A) or not (¬v A). B does not observe A's action while E does because of E's informational advantage.
If A violates the rules, Nature determines E's capacity to persuade A to come into compliance. E is able to inflict a large punishment ![]() $\overline e $ with probability q, or a small punishment
$\overline e $ with probability q, or a small punishment ![]() $\underline e $ with probability 1 − q, where
$\underline e $ with probability 1 − q, where ![]() $\overline e \gt \underline e $.Footnote 30 When E has more leverage over A and can punish A more severely by inflicting
$\overline e \gt \underline e $.Footnote 30 When E has more leverage over A and can punish A more severely by inflicting ![]() $\overline e $, it is more likely to persuade A to come into compliance. E observes A's type and whether it violates, along with its own type. If a violation occurred, E decides whether to reveal A's violation (r) or to obscure its information (o). If E publicizes the violation, A decides whether to come back into compliance with the law or to continue to violate it. If A continues to break the rules, it is punished, while if A comes into compliance, it is forgiven. Further, if E reveals the violation, B learns A's type and actions, whereas if A either does not break the law or does so but the violation is concealed by E, B does not observe A's decision. Finally, B decides whether to violate the rules (v B) or not (¬v B).
$\overline e $, it is more likely to persuade A to come into compliance. E observes A's type and whether it violates, along with its own type. If a violation occurred, E decides whether to reveal A's violation (r) or to obscure its information (o). If E publicizes the violation, A decides whether to come back into compliance with the law or to continue to violate it. If A continues to break the rules, it is punished, while if A comes into compliance, it is forgiven. Further, if E reveals the violation, B learns A's type and actions, whereas if A either does not break the law or does so but the violation is concealed by E, B does not observe A's decision. Finally, B decides whether to violate the rules (v B) or not (¬v B).
A's payoff is made up of four components. First, if A violates and E hides it, or if A violates at both of its moves, the state receives a net domestic benefit ![]() $b_A = \{ \overline b, \underline b \} $. Next, if B violates the rules, A receives utility from doing so as well because of its resulting enhanced capacity to defend itself against B, denoted d, and vice versa. If E publicizes A's violation and A does not come into compliance, A incurs a punishment of
$b_A = \{ \overline b, \underline b \} $. Next, if B violates the rules, A receives utility from doing so as well because of its resulting enhanced capacity to defend itself against B, denoted d, and vice versa. If E publicizes A's violation and A does not come into compliance, A incurs a punishment of ![]() $e = \{ \overline e, \underline e \} $, which captures the resulting economic sanctions or loss of reputation. If A rolls its violation back, however, it escapes punishment. Finally, A cares about the total number of states that comply with the agreement, represented by
$e = \{ \overline e, \underline e \} $, which captures the resulting economic sanctions or loss of reputation. If A rolls its violation back, however, it escapes punishment. Finally, A cares about the total number of states that comply with the agreement, represented by ![]() $\Omega _A(2 - 1_{\{ v_A\}} - 1_{\{ v_B\}} )$. This specification is in line with our discussion because the idea that actors gain more from obeying the law when others do also is central to this literature. Since this simple model consists of two potential violators, their utility from following the norm in effect depends on whether A and B themselves follow it.
$\Omega _A(2 - 1_{\{ v_A\}} - 1_{\{ v_B\}} )$. This specification is in line with our discussion because the idea that actors gain more from obeying the law when others do also is central to this literature. Since this simple model consists of two potential violators, their utility from following the norm in effect depends on whether A and B themselves follow it.
B's payoff depends on three items: it receives domestic costs and benefits from a violation that are summarized by the parameter B; it obtains d if both A and B violate the agreement since B can defend itself; and it derives greater utility the more states comply with the norm ![]() $\Omega _B(2 - 1_{\{ v_A\}} - 1_{\{ v_B\}} )$. Finally, E's utility is made up of two components: it cares about compliance with the law since E must enforce it, and it incurs a small cost s from the strategic obfuscation of a violation. The enforcer's utility function is thus
$\Omega _B(2 - 1_{\{ v_A\}} - 1_{\{ v_B\}} )$. Finally, E's utility is made up of two components: it cares about compliance with the law since E must enforce it, and it incurs a small cost s from the strategic obfuscation of a violation. The enforcer's utility function is thus ![]() $\pi _E(v_A,v_B,o) = \Theta _E(2 - 1_{\{ v_A\}} - 1_{\{ v_B\}} ) - s1_{\{ o\}} $.Footnote 31 This discussion is summarized in the game tree and the players' strategies are laid out fully in the appendix. We focus on pure strategy weak perfect Bayesian equilibria and solve the model through backward induction.
$\pi _E(v_A,v_B,o) = \Theta _E(2 - 1_{\{ v_A\}} - 1_{\{ v_B\}} ) - s1_{\{ o\}} $.Footnote 31 This discussion is summarized in the game tree and the players' strategies are laid out fully in the appendix. We focus on pure strategy weak perfect Bayesian equilibria and solve the model through backward induction.
Table 1. Model parameters

Assumptions and Discussion
We make several parametric assumptions. First, we assume that ![]() $\bar b - \bar e \gt \underline b - \underline e $ so that the difference in the potential domestic benefits associated with having nuclear weapons is greater than the difference between the two potential severities of E's punishment. Second, we assume that
$\bar b - \bar e \gt \underline b - \underline e $ so that the difference in the potential domestic benefits associated with having nuclear weapons is greater than the difference between the two potential severities of E's punishment. Second, we assume that ![]() $\underline b \gt \Omega _A(1)$ where
$\underline b \gt \Omega _A(1)$ where ![]() $\underline b $ is A's payoff if only A has nuclear weapons while ΩA(1) is A's payoff if only B has nuclear weapons. We thus assume that if only one country possesses nuclear weapons, A strictly prefers that A has them. Third, we assume that Ωi(.) is linearly additive, which ensures that a state's willingness to comply does not depend on the rate of noncompliance.Footnote 32
$\underline b $ is A's payoff if only A has nuclear weapons while ΩA(1) is A's payoff if only B has nuclear weapons. We thus assume that if only one country possesses nuclear weapons, A strictly prefers that A has them. Third, we assume that Ωi(.) is linearly additive, which ensures that a state's willingness to comply does not depend on the rate of noncompliance.Footnote 32
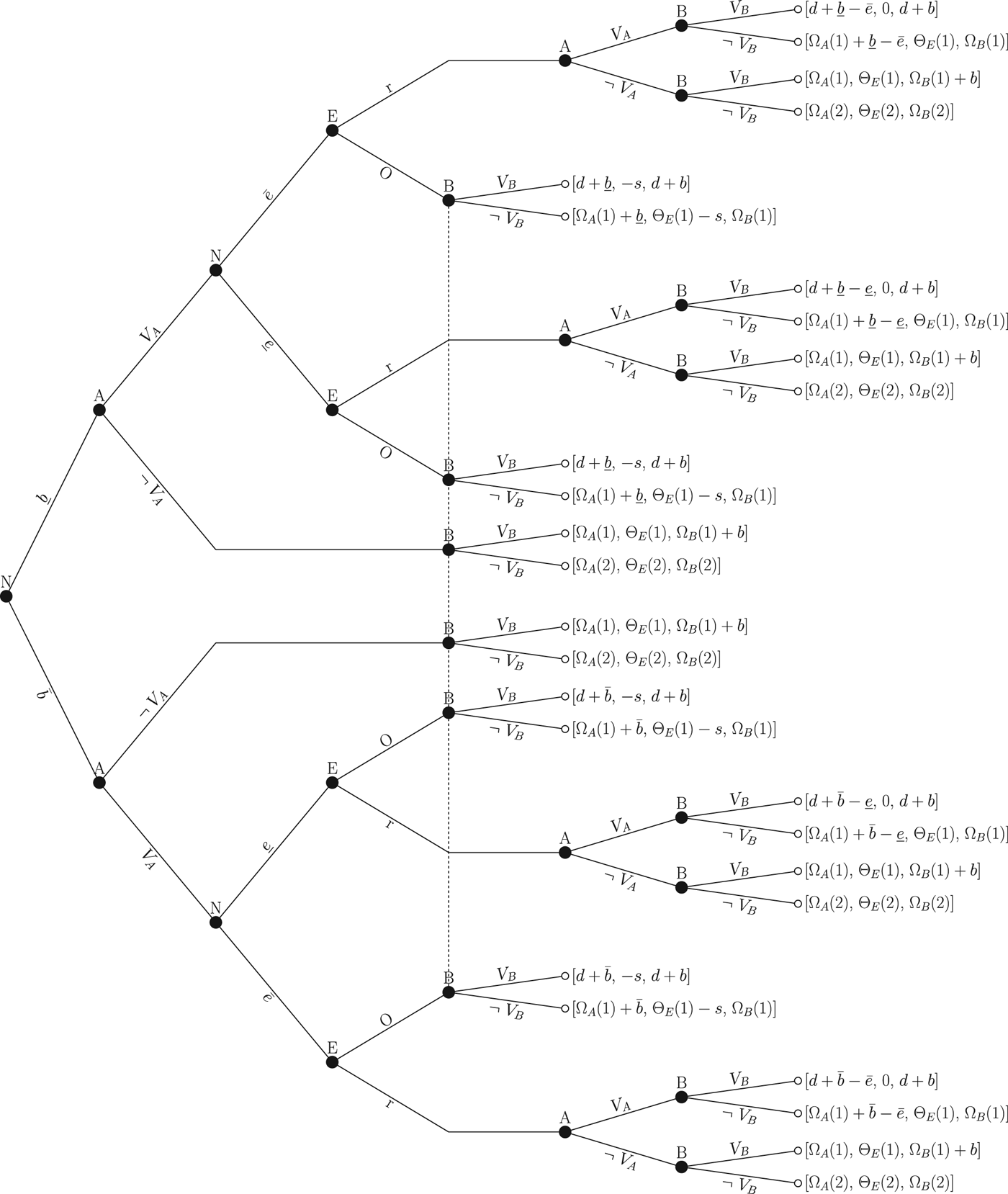
Figure 1. Game tree
We also make several simplifying modeling choices. First, we solve the game under imperfect information. Otherwise, if A's type were common knowledge, E's role would be minimal since B would know whether A violated the rules with certainty. Uncertainty about whether A desires cooperation—or whether B can “trust” A—is thus required for E to influence B's response. Moreover, we could instead assume that B obtains some information, or that E has imperfect information; the key assumption is that E possesses an informational advantage over B.
Second, we include only one B in the model, though typically many states are affected by A's decision in reality. A more complicated model could include additional Bs, though the intuition would remain the same. In such a model, E would not need to possess an informational advantage over all such states because E faces incentives to hide a given violation as long as doing so would affect the information received by at least one B.
Third, we conceptualize E as a state even though, as noted, international organizations and nongovernmental organizations also frequently possess information about compliance.Footnote 33 However, states have the capacity for strategic monitoring, while other actors often lack private information about compliance and thus cannot withhold it selectively.Footnote 34 We assume that evidence is necessary to change B's beliefs, so that E cannot alter its views by simply asserting otherwise. In effect, this means that E cannot lie, though this could be relaxed without changing the basic results.
Finally, E cannot publicize a violation if one did not occur. Since E must present evidence of a violation, we think it is reasonable to assume that E cannot lie, though this could be relaxed.
Analysis
While the full proof of the model appears in the supplemental appendix, we describe E's incentives and actions here. Specifically, consider E and B's responses to two scenarios: first, when A complies following E's threat to punish it, and second, when it does not. In the first case, E publicizes the violation. Then, B becomes aware that A is no longer breaking the law and therefore does not need to do so in self-defense. Further, A's capitulation preserves the norm so B continues to follow it since everyone else is doing so. Publicizing A's violation thus enhances the regime's health.
In the second case, publicity may still represent a rational response for E. The decision to hide A's activity may be exposed later, risking international and domestic criticism. However, if E publicizes the violation and A does not roll its program back, B may respond by violating the rules for two reasons. First, consistent with our threat mechanism described previously, B may require self-defense capabilities if A's violation poses a direct threat. Second, consistent with the pessimism mechanism, B may view the overall rate of compliance more negatively, and learn that the reputational consequences of violating the norm are not as severe as it thought. Whether this mechanism comes into play depends on the strength of the regime; if many other states follow the rules, the effect of A's violation is smaller than if few other states follow them. Thus, through both the threat and pessimism mechanisms, knowledge of a violation can weaken B's incentives to obey the rules.
By contrast, if E obfuscates the violation, B cannot detect it; it knows only that no violation was publicized. It thus believes that an infraction took place with some probability. Since A's transgression remains hidden, B is left with the impression of a greater consensus than if B knew that a violation occurred, creating stronger pressure to conform. Further, B's environment may be less threatening, since it is only possible that B faces a threat from A, rather than certain. The costs of violating the rules may not be worth addressing this potential threat, while they may be justified in the face of a known one.
When E observes a violation, then its best response depends on whether it can reverse A's decision and the likelihood that B will transgress following publicity. If B's self-defense needs are low and the regime is strong, such that B will not break the law regardless of A's actions, E always publicizes A's violation. Or, if E can reverse A's noncompliant behavior by exposing its violation, it will do so. However, if B would react to A's deviance by violating the rules itself, and E cannot reverse A's transgression, E hides the violation to avoid triggering the pessimism and threat mechanisms that might otherwise endanger the international regime. This discussion is captured formally by the following proposition and, under the assumptions listed previously, is summarized in Table 2:
Proposition 1
Assume d + b > ΩB(1) > b, ![]() $d + \bar b - \underline e \gt \Omega _A(2) \gt d + \underline b - \underline e $ and p[ΩB(1) − b] + (1 − p)(1 − q)[ΩB(1) − d − b] > 0.
$d + \bar b - \underline e \gt \Omega _A(2) \gt d + \underline b - \underline e $ and p[ΩB(1) − b] + (1 − p)(1 − q)[ΩB(1) − d − b] > 0.
Under these assumptions, E 's equilibrium strategy is to hide A 's violation if: 1) A will not come into compliance and 2) B will not violate if A 's violation is hidden. Otherwise, E publicizes the violation.
Table 2. Choice of strategic obfuscation versus publicity

While we have focused on the enforcer's incentives, the model is rich and provides many insights into issues such as overall regime stability. For example, the model also indicates that the possibility of obfuscation can erode the regime because B suspects that unobserved violations could be occurring but are hidden. Reliance on a monitor with less discretion, such as an IO, may help to mitigate this issue under some conditions. While we focus our empirical examination on E's strategic behavior, we address many of these additional implications later.
The Nuclear Nonproliferation Regime
We examine our model's predictions empirically by focusing on a particular international regime to make our problem tractable: the prohibition on the use of nuclear technology for developing nuclear weapons arsenals. Nuclear proliferation is a rich empirical setting in which to test our claims because it features powerful states—the US in particular—that sought to create and enforce a prominent and substantively important international regime affecting many countries over a long period of time. Moreover, it contains numerous cases in which the United States possessed unique, private information about other states' violations, giving it the opportunity to strategically choose whether to reveal this knowledge. Finally, the nuclear domain hosts variation in our critical independent variables and includes a corpus of recently declassified archival materials that permits us to examine the motivations behind these decisions.
The nonproliferation regime was formalized in 1968 in a binding multilateral agreement known as the Non-Proliferation Treaty (NPT). Since the treaty specifically regulates military uses of nuclear technology, we define a rule violation as the pursuit of nuclear facilities and nuclear-weapons-related research and development by any state besides the five classified as nuclear weapons states in the NPT (the US, Russia, the UK, France, and China.) Broad agreement exists that nonproliferation has become a strong norm,Footnote 35 and while the NPT did not create the norm, it “codified the sentiment that states should not seek to acquire nuclear weapons.”Footnote 36 Thus, though not all states signed the NPT, all were expected to abide by the rules of the nonproliferation regime more broadly.Footnote 37 Many scholars argue that normative and legal penalties for pursuing nuclear weapons constrain both their acquisition and use and that “violating these international norms will result in severe constraints to any state, such as political, economic and possibly even military reactions.”Footnote 38 This broad prohibition was reflected in the 1974 Zangger Committee's trigger list, under which members noted the importance of “the application of safeguards in non-nuclear-weapon states not party to the NPT,”Footnote 39 as well as in the norm's enforcement outside of the NPT more generally.Footnote 40
Monitoring of the norm takes place in part through the International Atomic Energy Agency (IAEA), which collects reports submitted by individual member governments, inspects their declared facilities, and conducts special inspections in response to particularly suspicious member activities. In practice, however, its activities are limited, particularly during the period we analyze, because “IAEA safeguards inspections had been quite pro forma. IAEA inspectors only checked on nuclear facilities that states chose to declare; they typically did so in a ‘cursory’ manner, and up to 1991 they had never undertaken even a single ‘special inspection’ of suspect facilities … Essentially, the regime was strong enough only to ensure that the IAEA would become aware of a ‘smash and grab’ operation on declared nuclear fuel within six months of its occurrence.”Footnote 41 As a result, effective monitoring typically depends on intelligence collected by member states.Footnote 42 We focus on the US in particular because it devotes substantial resources to tracking nuclear programs, possesses superior intelligence, and exercises greater discretion about whether to publicize that information.Footnote 43
Empirical Analysis
We test an implication of our argument that is normally difficult to observe: whether a well-informed state that both supports and helps to enforce the regime (E) manipulates its private information consistent with the conditions that we derive in the model. The model suggests that when B mistrusts A and has an incentive to arm if A does, it should develop nuclear weapons since it assumes that A likely violated the norm. However, if B has relatively high trust in A and seeks weapons only if A has them, it should not pursue them in the absence of additional information. The key implication is that if an enforcer publicizes A's decision to proliferate and cannot convince A to reverse its program, B will seek its own arsenal when it otherwise would not have. In such a scenario, the enforcer will obfuscate A's activities to prevent B's reactive defection.Footnote 44 Otherwise, we expect the enforcer to disclose information in line with the conventional wisdom.
Our empirical strategy draws heavily on declassified American intelligence and related documents. This primary evidence helps us to accomplish three goals: we identify cases in which a state's intelligence was withheld despite the difficulty in observing such cases using traditional open sources; we test the theory by evaluating the conditions under which intelligence was hidden; and we test our theoretical mechanisms by assessing leaders' intentions and beliefs about the consequences of their actions.Footnote 45 The United States was a key regime advocate throughout the period we analyze and often had private information about other states' nuclear activities that allowed it to make strategic decisions about how to handle violations of the nonproliferation norm.Footnote 46 In each case we analyze, the US had an informational advantage over both the IAEA and most other states, though it did not necessarily possess an informational monopoly, which is not necessary for the enforcer to hold and exercise such an advantage.Footnote 47
Our specific research question narrows the relevant universe of cases to: (1) states that pursued a military nuclear capability; (2) states with clandestine programs that were active after the emergence and formalization of the norm against proliferation; and (3) states that had not overtly demonstrated a nuclear weapons capability through a test or a political announcement.Footnote 48 These criteria include the nuclear programs of states outside of the NPT, for both empirical and theoretical reasons. Empirically, the prohibition on new arsenals since 1967 has been treated as universal (as we discussed previously) and, as our case evidence demonstrates, key states perceived nonmembers' programs to be central to the fate of the nonproliferation regime. Theoretically, including nonmembers is important because previous studies of naming and shaming have explicitly identified publicity as a useful tool for convincing new states to join the regime. Table 3 lists the resulting universe of cases.Footnote 49 Because we require access to internal assessments and discussions, we take advantage of the recent release of declassified material on US views of nuclear proliferation trends, supplementing these data with secondary sources where necessary.Footnote 50
Table 3. Choice of strategic obfuscation versus publicity

Note: The table shows which cases featured conditions that should have led E to strategically obfuscate (lower-right box) or publicize violations (other three boxes).
Our main independent variables are the perceived likelihood that the proliferator would comply following publicity (i.e., A's reversal), and the perceived risks of second-order proliferation (i.e., B's reaction). The former is coded using US assessments of this probability. Since the US generally believed that compliance was more likely when the US possessed strong unilateral leverage over the country and when a multilateral coalition could be assembled in opposition to the program, we note when either of these factors were present.Footnote 51 In such cases, tactics such as diplomatic pressure and threats of sanctions were frequently effective. However, the primary determinant of how this variable is coded is whether the internal US assessments indicate a belief that compliance was likely.Footnote 52
The risk of reactive proliferation is coded in two parts. First, we assess the US's belief that other states would react to a violation by pursuing nuclear weapons and/or hosting an existing nuclear power's nuclear weapons.Footnote 53 Specifically, we code the regional threat as “low” if it was deemed unlikely that other states would proliferate in response, “medium” if one other state might have done so, and “high” if more than one other state was expected to respond by proliferating.Footnote 54 Second, we determine the strength of the regime at the time of the violation, which we simplify by coding three phases following Wan.Footnote 55 Phase I includes 1968–1978, which encompasses the date the NPT entered into force through a period of reforms to strengthen the regime that took place in the 1970s.Footnote 56 Phase II includes 1979–1990, a period that featured only minor changes to the regime. Phase III includes 1991 and beyond when major reforms were implemented that were catalyzed by the 1991 Gulf War,Footnote 57 and the Cold War's end left the US as the sole superpower, facilitating multilateral pressure on violating states. If neither of these two components are coded as “high,” then this variable is coded as “low.”
Finally, for our dependent variable—the US's (i.e., E's) reaction to each violation—we code whether the US chose to publicize or conceal its private assessments of each state's nuclear activities. Publicity occurred when the US shared its private information through bilateral contacts with other governments, international organizations, official public media statements, or authorized leaks by government officials.Footnote 58 The US engaged in the strategic obfuscation of another state's noncompliance when it attempted to minimize the scrutiny of the violation and abstained from sharing private information about the program at any time following a state's initial violation.Footnote 59
We analyze each case and organize our empirical analysis according to the four scenarios shown in Table 3. As Table 4 summarizes, we find that the US strategically obfuscated violations in five cases: Israel, Pakistan, India, Iraq (pre-1990), and South Africa. In the remaining examples, the US chose to publicize states' noncompliance. We analyze the full universe of cases, though space constraints limit our presentation to exemplar cases from three of the four potential scenarios shown in Table 3. We assess the remainder in the appendix.Footnote 60
Table 4. Summary of cases
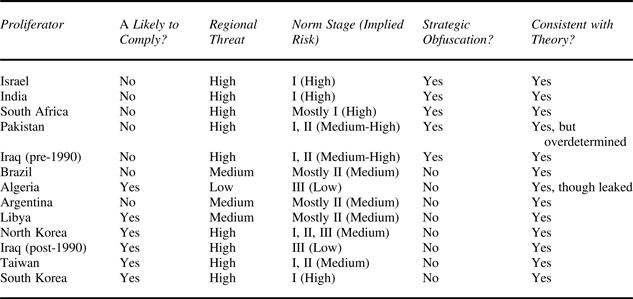
Notes: The table summarizes the coding of each of our cases. The fourth column codes the norm stage as described in the text, and in parentheses we list the resulting severity of the threat of reactive proliferation.
Israel (Proliferator Unlikely to Comply and High Risk of Reactive Proliferation)
When the threat of reactive proliferation is high and the violator is unlikely to comply following US efforts to compel it to do so, our theory expects the US to strategically obfuscate the infraction since publicizing it would sharpen the threat posed to regional rivals and weaken other states' confidence in the norm. We find that these conditions held in five cases and that the US chose to conceal the state's activities in each. We focus on Israel here and analyze the others in the appendix.
The US's confidence that Israel was clandestinely progressing toward a nuclear arsenal grew in a political climate marked by strong concerns about larger proliferation trends.Footnote 61 This period marked the earliest, most fragile stage of the norm. Since relatively few states adhered to it, a single deviation could have revealed the norm's weakness and shown states that the consequences from violating it were less severe than they previously thought. As early as 1961 the US had concluded that Israel would obtain plutonium by 1965–66 and would have a weapon by 1966–67. By 1969, the US had determined that Israel possessed a weapon.Footnote 62
The US was convinced that Israel was highly unlikely to relinquish its program despite the US's efforts to convince it to do so, such as threatening to curtail the US's support for Israel and offering security guarantees, military assistance, and foreign aid.Footnote 63 US intelligence officials believed that even regional diplomatic solutions like a Middle East peace agreement would not change Israel's course; open pressure or a multilateral coalition were seen as futile.Footnote 64 Henry Kissinger concluded that it was “impossible to deprive Israel of the option to put together an operational nuclear capacity” because it would be “impossible politically for an Israeli Prime Minister to give up completely an advantage deemed vital and achieved at considerable cost … [the US] has no way of forcing Israel to destroy any nuclear devices or components it may now have.”Footnote 65
Thus, while the US had kept estimates of Israel's nuclear program secret since 1960,Footnote 66 a September 1969 visit by Israeli Prime Minister Golda Meir made this secrecy permanent in an agreement to hide Israel's nuclear status.Footnote 67 Evidence for both the pessimism and threat mechanisms is showcased during debates surrounding this meeting. Obfuscation advocates argued that avoiding the publicity of Israel's nuclear arsenal would reduce the chances that surrounding states that were hostile toward Israel would reject the NPT to seek their own nuclear capabilities. Cohen notes that “the most serious concern … was that the Israeli nuclear project would lead to a dangerous regional nuclear arms race.”Footnote 68 US leaders feared that Syria and Egypt might seek a Soviet nuclear security guarantee because of the direct threat that Israel's activities posed. As Kissinger's top adviser on the Middle East wrote, “Until the Arabs could develop nuclear weapons, they might seek, and get, Soviet agreement to extend a ‘nuclear umbrella’ to the Arab states.”Footnote 69 Publicity would exacerbate this because the Soviet Union might find it harder to decline such a request once Israel's arsenal became an established fact and, over time, other Arab states could seek their own nuclear capabilities.Footnote 70 Kennedy also expressed concerns that Egypt would respond by developing a nuclear weapon, and the US worried about the possibility of a nuclear arms race among Arab states more generally.Footnote 71
The US also worried about the reaction of states that were further afield, since they might believe that the emerging nonproliferation norm had weakened and would likely feel less pressure to adhere to it themselves. For instance, an issue paper widely circulated within the Nixon administration claimed that Israel's nuclear arsenal could jeopardize the momentum toward global acceptance of the treaty. Similarly, a State Department policy planning staff memo argued, “A known Israel nuclear capability would have far-reaching unfavorable effects,” first among them that “other nuclear capable countries would be more likely to opt in favor of nuclear weapons for themselves and … would be less likely to sign the NPT.”Footnote 72 Indeed, internal documents show that leaders outside of the Middle East considered reactive proliferation. For example, the West German chancellor cites the possibility of Israel's proliferation as a key consideration in Germany's nuclear pursuits.Footnote 73 The US intelligence community, too, argued that an awareness of Israel's activities might cause changes in general perceptions of proliferation trends that could be detrimental to the norm.Footnote 74 The New York Times reported, “American officials are particularly worried about the pressures that [Israel's possession of the bomb] may put on such countries as India, Japan and Sweden, which are believed to have the technical capacities for producing atomic arms, but are not believed to have done so.”Footnote 75
The US thus created “circumstances in which Israel would not ‘announce’ a nuclear capability and would maintain secrecy” through “private, bilateral assurances that Israel would not deploy or test nuclear explosive devices.”Footnote 76 Indeed, “Nixon probably guaranteed that the United States would not pressure Israel to roll back its program and join the NPT if it kept a low profile; this entailed a non-testing and non-declaring guarantee.”Footnote 77 As Kissinger succinctly stated in the summer of 1969, “public knowledge is almost as dangerous as possession itself.”Footnote 78 A subsequent memo from Kissinger reminded Nixon that during his visit to Israel he had “emphasized [to Meir] that our primary concern was that the Israelis make no visible introduction of nuclear weapons or undertake a nuclear test program.”Footnote 79 While other states might suspect that Israel had nuclear weapons, the US hoped that enough doubt would remain to dissuade reactive proliferation.Footnote 80 Kissinger argued,
Our interest is in preventing Israel's possession of nuclear weapons. But since we cannot—and may not want to try to—control the state of Israel's nuclear program and since Israel may already have nuclear weapons, the one objective we might achieve is to persuade them to keep what they have secret. This would meet our objective because the international implications of an Israeli program are not triggered until it becomes public knowledge … . Our aim is to keep Israel's possession of nuclear weapons from becoming public knowledge and to do what we can to stop further proliferation.Footnote 81
Although many leaders suspected that Israel intended to acquire a weapon—Egypt's Nasser had publicly warned the Arab world about a possible future Israeli arsenal in 1960—the US thought that hiding the weapons program could “keep Israeli possession from becoming an established international fact.”Footnote 82 While information about the arsenal was leaked to the New York Times in 1970, we find no evidence in the sourcing of this story or histories of this period that this was an authorized leak used to place pressure on Israel. Since the US intended to keep the secret, this case is coded as an example of concealing the violation. The US assumed that some leaks would take place, as “news about Israeli progress could continue to seep out … until it is generally taken for granted that Israel has this capability”Footnote 83 but the US administration hoped that “‘other nations might be kept in line,’ and nuclear weapons acquisition might be delayed ‘at least five to ten years.’”Footnote 84
Brazil (Proliferator Unlikely to Comply but Low Risk of Reactive Proliferation)
When the threat of reactive proliferation is low, the US should publicize programs even when the proliferator is unlikely to comply with the US's demands. This strategy avoids the international and domestic scrutiny that occurs if obfuscation of the violation is later exposed, along with the costs of convincing the proliferator to keep its program secret. These conditions held in two closely linked cases—Argentina and Brazil. We focus on Brazil here and analyze the Argentina case in the appendix.
Brazil began constructing a nuclear power plant in 1971, and by 1983 the US had determined that it could produce highly enriched uranium by the mid-1990s. The program remained secret throughout the 1970s and 1980s before it was dismantled in 1990. While Brazil acquired the technology to produce nuclear weapons, it did not build them and instead acceded to the NPT in 1998. The US determined that while Brazil was unlikely to comply as a result of US efforts, the threat of reactive proliferation was relatively low (with the possible exception of Argentina, which we detail subsequently), so the US did not hide the program.
The US argued that Brazil would not come into compliance as a result of US publicity and pressure, stating that Brazil would “persist in its … resistance to any US effort to constrain its nuclear ambitions.”Footnote 85 Furthermore, US officials claimed, “Brazil strongly resists what it perceives as foreign effort to limit its access to new equipment and technologies.”Footnote 86 Intelligence officials concluded, “It will be difficult for the United States—or any other nation—to have a major impact on its nuclear policies … Brazilian leaders have a strong determination to pursue their own self-interest—especially with regard to the acquisition and development of nuclear technology—and the confidence to oppose those who stand in their way.”Footnote 87 Brazilian officials echoed these sentiments. For instance, a Brazilian embassy representative stated, “We know how to resist any and all US pressures … Our nuclear program will continue, at least to the extent it depends on us, against all internal and external pressures.”Footnote 88 US coercion and its publicity of the program did not compel Brazil's compliance, but instead propelled Brazil and Argentina to work together. While the two states had faced a brief period of tension over hydroelectric resources, US pressure made both so angry that they overcame their differences to cooperate in the nuclear domain.Footnote 89 A multilateral coalition was also unlikely to form since states were divided over whether to support Brazil's nuclear program. For example, West Germany and China assisted Brazil, while the Soviets joined the US in opposing it.Footnote 90
Although obtaining Brazil's compliance was improbable, the threat environment was also not particularly high, leading the US to expose the violation. First, because the norm was in its intermediate stage, the threat of a defection to the overall regime was moderate since a single defection would be unlikely to significantly change states' views of the likely consequences. Second, Argentina was the main concern regarding second-order proliferation, since Brazil's activities could directly threaten the state. Yet “neither Argentina nor Brazil perceived the other as having the intention to introduce instability into the Southern Cone by building nuclear weapons.”Footnote 91 Instead, they held talks beginning in 1967 that helped to ensure that nuclear energy would be used for peaceful purposes.Footnote 92 Although the talks had several fits and starts, they picked up in the early 1980s and continued until the dismantling of the programs. This “fluid dialogue … kept both sides comfortably aware of their counterparts' intentions and capabilities and prevented the development of a nuclear rivalry.”Footnote 93 Brazil and Argentina's nuclear interests appeared to be safely short of weaponization because “the Brazilian military sought to reach the same technological level that Argentina was on the verge of achieving: that of enrichment capacity and the resulting nuclear option. In this regard the technology itself was seen as a ‘species of deterrent’; the mere capacity to match a potential Argentine bomb was presumed sufficient to deter its construction.”Footnote 94 The US therefore believed that “relations between the two nations are marked by intermittent rivalry rather than overt hostility”Footnote 95 and chose not to hide Brazil's program.
South Korea (Proliferator Likely to Comply)
Our theory expects the US to publicize a violator's activities regardless of the threat of reactive proliferation if the US is likely able to compel compliance. The US was confident that it could do so in six cases: North Korea, Iraq after 1990, Taiwan, South Korea, Libya, and Algeria. To illustrate the common logic leading to the publicity of these programs, we assess the South Korean case here and analyze the remaining cases in the appendix.
The US correctly ascertained that South Korea was moving toward obtaining a nuclear weapon in 1975.Footnote 96 The threat environment was high both because the risk came during Phase I of the norm's development—so a single defection could signal weak social consequences for doing so—and because the US feared proliferation by nearby states for whom a violation by South Korea would represent a direct threat. US internal policy memos highlighted the danger, stating, “Our general concerns are intensified by … the impact which any Korean effort to establish nuclear capability would have on its neighbors, particularly North Korea and Japan. ROK [Republic of Korea] possession of nuclear weapons would have [a] major destabilizing effect in an area in which not only Japan but USSR, PRC, and ourselves are directly involved. It could lead to Soviet or Chinese assurances of nuclear weapons support to North Korea in the event of a conflict.”Footnote 97
However, the US expected public scrutiny and its own private threats to lead to compliance. Policy officials explained, “We believe that [a] direct, early, and firm approach … will have best chance of success.”Footnote 98 The US thus advocated for “several complementary policy courses … [that would] be evolved inside of, or in consonance with, the multilateral framework.” These policies included working with other nations to “inhibit ROK access to sensitive technology and equipment, … press the ROK to ratify the NPT, [and] improve our surveillance of ROK nuclear facilities.”Footnote 99 The US had strong leverage over South Korea as its biggest trading partner, primary buyer of South Korean debt, large provider of aid and nuclear materials, and military guarantor. Further, because of South Korea's reliance on the US's nuclear umbrella, security guarantees were thought to be a particularly effective inducementFootnote 100 as a result of “the US rapprochement with China and withdrawal from Vietnam, both of which communicated to South Korea that anti-Communism was no longer sufficient to merit unwavering military and political support from the US.”Footnote 101 The US acted on this leverage in various ways, such as making Export-Import Bank loans for the country's nuclear industry contingent on NPT ratification, threatening to cut its annual $225 million in military assistance, and threatening to restrict technology sharing, financing, nuclear cooperation, and security guarantees.Footnote 102 Reagan also promised security guarantees and economic support to reward South Korea's compliance.Footnote 103 This strategy succeeded. “Under US pressure, in January 1976 it suspended negotiations for a reprocessing facility; in December 1976 it suspended the whole formal program to develop nuclear weapons technology that it had inaugurated only two years earlier.”Footnote 104
Its close political relationship with South Korea not only provided the US with leverage but also necessitated a discreet method of publicizing its potential proliferation. Because of the US–South Korean partnership during the Cold War, the US believed that explicit and official public criticism of Seoul's nuclear program was unwise. Instead, US policymakers quietly consulted with potential nuclear suppliers and indirectly publicized its activities through authorized leaks to the media. For example, major news headlines at the time warned of South Korea's nuclear ambitions and France's cooperation on reprocessing technology citing “high-ranking Administration officials” as sources.Footnote 105 Thus, while the US used an ally-friendly publicity strategy, the overall approach comports with the theory's predictions.
Possible Alternative Explanations
The results of the case study analysis are largely consistent with our theoretical hypotheses. The US withheld private information on noncompliance when it faced a hard-to-reverse proliferator and probable reactive proliferation. In the absence of these conditions, the US tended to publicize its private information. This basic logic also appeared in broader private US assessments of nuclear proliferation. Two classified American intelligence reviews of overall proliferation trends show a widespread perceived link between the publicity of nuclear activity and the health of the regime. For example, a 1975 CIA analysis of proliferation trends invokes the logic of the pessimism mechanism, arguing that the US should seek to “delay … successive nuclear debuts to prevent or reduce the momentum of change.” It concludes that if proliferating states “leave their nuclear status purposely ambiguous,” then “the rate of proliferation … would itself be ambiguous and threshold states would react to the suspicion rather than the demonstrated certainty of nuclear debuts.”Footnote 106 A classified assessment of proliferation trends from the mid-1980s similarly notes that “the norm against developing weapons may become psychologically harder to breach the longer it persists overtly unbroken.”Footnote 107 It further assesses that the US's efforts to avoid and delay visible violations of the norm “lessened the adverse impact their development of a nuclear capability otherwise would have had on the international system for containing proliferation.”Footnote 108 Note that these conclusions were not intended for public consumption; they represent candid internal judgments about the value of past US efforts to avoid public, overt violations of the nonproliferation regime.
We also consider several alternative explanations of the patterns that we observe. One possibility is that the US strategically obfuscated violations by its allies and publicized those of its adversaries or its adversaries’ clients. This is plausible in part because US domestic law requiring sanctions for proliferation raised the stakes of publicly acknowledging an ally's nuclear program; the Cold War also increased the cost of alienating friends. Yet the evidence casts doubt on the power of this explanation. Two countries whose violations were obfuscated, Iraq and India, were not US allies. Other key proliferation cases involved political relationships that fluctuated during the Cold War. For example, the US's views of states like South Africa and Pakistan changed significantly as a result of shifting geostrategic and presidential priorities.Footnote 109 Recent work suggests that states are more likely to proliferate when they are less dependent on the US because the US maintains weaker leverage over them.Footnote 110 Even in a case like Pakistan where this alternative explanation has some purchase, we still find archival material consistent with the theory's mechanisms. Thus, even if these considerations occasionally play a role, they do not explain the observed variation across cases.
Another potential alternative explanation is that the US obfuscated to avoid looking weak when it was unable to reverse a program; otherwise, publicity risked humiliation. However, many of the cases we analyze do not fit this logic. For instance, the US publicized Argentina and Brazil's efforts but did not believe it could roll back their programs. The US often applied sanctions ineffectively to deter potential future proliferators, demonstrating that it was not deterred from punishing states by the slim chance of success.Footnote 111 Finally, we found little to no discussion of these concerns in our primary or secondary documents.Footnote 112
A third possible alternative is that the US strategically obfuscated violations by states that were not formal members of the NPT because such deception was unlikely to be discovered by the IAEA. We do not think this consideration played a significant role for several reasons. First, the empirical pattern does not comport with this explanation. For example, the US hid Iraq's program even though it was an NPT signatory, while the US publicized Argentina, Brazil, and Algeria's programs even though these states were not signatories at the time. Second, as we mentioned earlier, the IAEA had very limited information-gathering capabilities for members and nonmembers during the period we analyze. Since the IAEA was restricted to routine inspections and declared facilities, US leaders could be reasonably confident that the information they gleaned from confidential sources and methods would not be discovered by the organization regardless of the state's NPT status. As one former IAEA director-general explained, during the 1970s and 1980s, “for regimes that chose to conceal their illicit activities, the IAEA was a beat cop with a blindfold.”Footnote 113
Discussion: Potential Regime Erosion
The model and case studies support our core claim that well-informed states strategically exercise informational discretion to buffer regimes from problematic cases of noncompliance, but what effect might this practice have on a regime's long-term health? After all, reliable information about noncompliance can reassure states that they will not become victims of undetected defection and that violators will be punished. The formalization of our theory suggests that a potential downside of an enforcer's ability to hide infractions is an erosion of compliance within the regime.Footnote 114 If it is possible for the enforcer to hide noncompliance, states may infer that unobserved proliferation is taking place, creating a possible risk of reactive proliferation when no initial proliferation took place. The enforcer cannot credibly commit ex ante to reveal all infractions because once it detects a breach that it cannot roll back and that will lead to further proliferation, it faces strong short-term incentives to obfuscate it.Footnote 115 In contrast, if the enforcer reports all violations, member-states will feel more confident that unobserved proliferation is not taking place. Yet, as we have described, this will include exposure of violations that likely cannot be reversed and that risk creating reactive violations that endanger the regime.
An enforcer's ability to exercise discretion about whether to reveal information thus creates a trade-off, mitigating some dangers to the regime while enhancing others. These costs and benefits associated with strategic monitoring may help to shed light on questions surrounding institutional design, including recent moves toward a more aggressive monitoring role for the IAEA. Delegating the capacity to gather compliance-related information to IOs may make strategic obfuscation less likely as many states are involved in IOs' operations and their conclusions are typically more transparent than those of states. Since the IAEA's powers increased after 1990, the potential for obfuscating nuclear programs has likely been reduced. A plausible interpretation of the IAEA's evolution is that it was prompted, at least in part, by fears of regime erosion resulting from the US's efforts to hide several defections.Footnote 116 Assessing the downsides of strategic obfuscation and its impact on decisions to delegate monitoring remains an interesting direction for future research.
Conclusion
Shining a light on violations of social rules is often thought to foster compliance and build social order. This logic is manifested in models of norm emergence, international legal compliance, and theories of the cooperation-enhancing function of international organizations. Although there is truth to this view, the full picture is more complex. Drawing on studies both within and outside of political science, we developed two mechanisms through which the publicity of rule violations can endanger international regimes. It can alert neighbors and enemies to the direct threat posed by a state's deviance and can create pessimism about the overall rate of compliance, lessening the perceived social opprobrium that results from a violation. We modeled these dynamics to identify the conditions under which a well-informed state might manipulate its private information about infractions to avoid triggering these dynamics. The model shows that such a state does so when it cannot reverse a violator's activities and when those activities would create additional defections if they were revealed. We found considerable support for our core hypothesis in our examination of how the US has handled information about nuclear proliferation. However, we also discussed our model's insight that the concealment of violations can possibly erode the regime over time.
While we focus on the nuclear setting, our theory's mechanisms are relevant for a wide range of empirical domains, though some areas may support the threat and pessimism mechanisms differently. In particular, the greater the negative externalities associated with a given violation, the more relevant the threat mechanism becomes. Yet this is a modest scope condition because defections impose direct harm to other states in many if not most areas of international laws and norms including those governing security, economic, and environmental issues. A required condition for our central empirical prediction is that the enforcer must possess information advantages that create opportunities for exercising discretion over whether to report violations. This also represents a modest condition since many states hold information advantages—even if only temporarily—about economic and security-related activities that confront leaders with meaningful choices about whether to publicize their knowledge. Even when information advantages are rare, our mechanisms linking the publicity of infractions with compliance behavior apply.
This article suggests the substantive importance and theoretical promise of addressing secrecy and strategic information management in studies of international compliance. Potentially fruitful extensions of our theory include investigating dynamics in a world with multiple regime enforcers, and the domestic political concerns associated with hiding violations.Footnote 117 Scholars could also incorporate new technologies or practices into the theory such as social media and unauthorized leaks because these developments could reduce states' informational discretion and therefore shrink opportunities to obfuscate violations. Finally, while we have demonstrated our theory's application to the nuclear domain, our model could be productively tested in many other empirical arenas as well.
Supplementary Material
Supplementary material for this article is available at <https://doi.org/10.1017/S0020818318000176>.







