Introduction
In response to the COVID-19 pandemic, many countries developed and deployed digital contact tracing (DCT) systems utilizing data collected from users’ mobile phones. This paper describes the laws and policy instruments employed by nine countries to authorize and regulate the use of DCT technology. Our analysis provides an overview of the governance approaches adopted by countries in the design and implementation of DCT technology. We found that the countries surveyed employed one of two distinct governance approaches: a Data Protection Model, focused primarily on legislative instruments aimed at creating a legal basis for DCT systems in the context of rigorous data protection and privacy safeguards; or an Emergency Response Model, focused on expanding executive prerogatives with the aim of gathering as much data as efficiently as possible to help prevent the spread of COVID-19. Analyzing the strengths and weaknesses of these contrasting DCT governance models should contribute to developing more nuanced governance approaches for the future use of DCT, as well as other digital public health technologies.
Our analysis suggests that neither the Data Protection Model nor the Emergency Response Model was ideally suited to the governance of DCT. Emergency response laws provide few protections against the government’s use of citizens’ data, prompting concerns about lack of transparency and accountability. Data protection laws, on the other hand, are designed primarily to protect against invasions of users’ privacy; yet in a critical pandemic, there may be overriding public health goals that render the privacy objective more of a hindrance than a societal benefit.
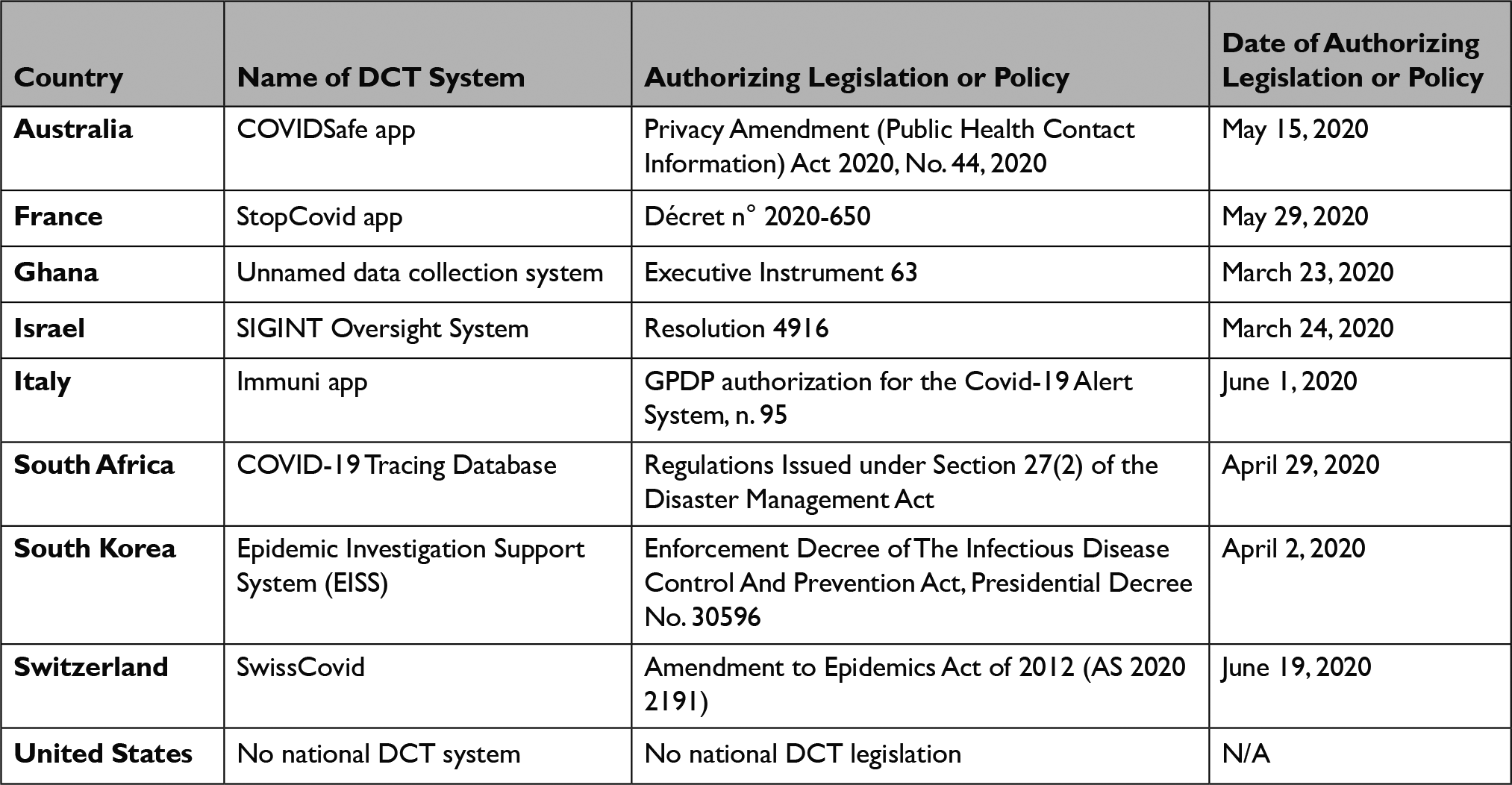
This paper surveys the governance approach employed by nine countries that utilized mobile phone-based DCT technology in response to COVID-19: Australia, France, Ghana, Israel, Italy, South Africa, South Korea, Switzerland, and the United States.
We argue that a new approach to DCT governance is needed to maximize the benefits of this technology for future infectious disease outbreaks. Current research suggests that DCT employed during COVID-19 helped to reduce transmission when the system was widely adopted;Reference Ferretti1 but low uptake tended to undermine effectiveness.Reference White and van Basshuysen2 Governance of DCT must strike the right balance between mandating use of the technology and fostering trust and voluntary adoption. Governments must implement oversight and accountability mechanisms, prevent the misuse of personal data, provide transparency regarding the functionality of DCT, and deploy an effective communication strategy to explain the public health uses and benefits of the technology. We recommend that, as we move beyond “first generation” DCT, countries that utilize DCT technology in the future develop a tailored governance approach capable of effectively regulating and communicating about this new form of public health intervention.
1. Contrasting Governance Models
Contact tracing is a public health tool that is traditionally employed by public health agencies to identify and alert individuals who have been exposed to an infectious disease agent in order to recommend or impose quarantine or other measures designed to limit further spread of the pathogen.Reference Klinkenberg, Fraser and Heesterbeek3 “Digital contact tracing” (DCT) refers to a broad category of technologies used to facilitate the identification of individuals who may have been exposed to an infectious agent such as the virus that causes COVID-19, SARS-CoV-2. DCT is a novel form of technology that holds promise to valuably automate and scale up traditional public health contact tracing. Although there were earlier, smaller-scale earlier attempts to use DCT,4 the COVID-19 pandemic prompted a much more significant effort on the part of many national governments to collect data via mobile phones to augment traditional contact tracing on a large scale.
This paper surveys the governance approach employed by nine countries that utilized mobile phone-based DCT technology in response to COVID-19: Australia, France, Ghana, Israel, Italy, South Africa, South Korea, Switzerland, and the United States. (Each country’s approach to DCT governance is summarized in Table 1, below.) Because France and Italy are members of the European Union (EU), we also discuss the EU’s approach to DCT governance. We selected these nine countries based on their geographic diversity and the public availability of relevant legal materials accessible to members of the author group. All of these countries, except for the United States, enacted legislation or policy at the national level that was specifically tailored to authorizing and regulating the use of DCT in response to COVID-19. These DCT-specific laws fell into two categories. In Australia, France, Italy, and Switzerland, the government authorized the use of DCT by enacting laws designed to be consistent with existing data protection laws. The remaining four countries — Ghana, Israel, South Korea, and South Africa — authorized the use of DCT under their emergency response laws. We discuss each group in turn.
1.1 The Data Protection Model
The countries discussed in this section adopted a “Data Protection Model” of DCT governance. This model has two distinctive features: First, the countries that adopted this model enacted DCT-specific laws as amendments to or ordinances under existing data protection laws. Second, the model is grounded in the principle of data minimization, which holds that the least possible amount of personally identifiable information necessary to achieve a given purpose should be collected, used, and disclosed.
The European Union
The European Union (EU) adopted governance of DCT technology by means of guidance issued by the European Commission (EC) on April 17, 2020 (2020/C 124 I/01).5 The EC guidance identifies privacy and data protection as paramount policy concerns in implementing DTC. In particular, the EC guidance stresses the importance of data minimization and sets very rigid limits for data disclosure, use, and storage, consistent with the EU’s regulation governing the protection of personal data, the General Data Protection Regulation (GDPR).6
The EC Guidance tends to support a “decentralized” approach to DTC, in which data collected from mobile phone users is stored in their phones and contact tracing is activated from that locally stored data. This is in contrast to a “centralized” approach in which data are transmitted to a central database where contacts between users are identified and from which contacts with infected users are notified to those exposed. The EC left member states leeway to adopt either the centralized or decentralized approach.
During the early weeks of the pandemic, a group of European IT experts had created a consortium, known as Pan-European Privacy - Preserving Proximity Tracing protocol (PEPP-PT), which aimed at developing a centralized DCT protocol. Countries such as Germany, France, and the United Kingdom had already begun the development of their national DCT systems based on such a protocol, when another group of experts (some initially part of PEPP-PT) formed an alternative consortium focused on the creation of a decentralized model: the Decentralized Privacy-Preserving Proximity Tracing, or DP-3T for short. DP-3T also included experts from outside the European Union, including from the Swiss Federal Institutes of Technology of Lausanne (EPFL) and Zurich (ETH). Based on specifications from the DP-3T protocol, Google and Apple created an API for the development of apps on mobile phones running Android and iOS, which is known as the Google Apple Exposure Notification (GAEN) system.
The GAEN system relies on low-energy Bluetooth signals sent between mobile phones to record “proximity events,” that is, instances in which a user is in proximity to another user, usually defined as within six feet or two meters for a specified period of time (e.g., 15 minutes). When a proximity event occurs, the users’ phones exchange encrypted “tokens,” each of which corresponds to the other user’s cell phone but is anonymous as to the other user’s identity. These tokens are stored on the users’ phones for a specified period of time (e.g. 14 days). Users are instructed to report into the GAEN app on their phone if they test positive for SARS-CoV-2. If a user reports a positive test, all other users who have the infected user’s token stored on their phone receive push notifications warning them of their potential exposure, but without revealing any information about the time of the exposure or the identity of the contact.Reference Apple7 The GAEN system is “decentralized” because the record of these proximity events is stored exclusively on the various users’ phones, not in a government or corporate database.
Italy
The availability of GAEN induced some European countries, including Italy, to adopt a decentralized approach to DCT. In June 2020, Italy released an app called Immuni based on the GAEN system. The legal basis for the Immuni app was an executive decree, issued by the Government on April 30, 2020 to specify the legal framework for the use of a national contact-tracing app and to address particular issues regarding accountability and data protection and privacy, in compliance with the GDPR.8 The decree provides that: (1) the technical platform of the Italian DCT system should be entirely located on the national territory, (2) clear and exhaustive information should be provided to users before the activation of the app, (3) only essential data may be collected, which may not include user geolocation data, (4) the collected data may be used only for specified purposes and should be regularly erased, and (5) the system should be deactivated by the end of 2020. On June 1, 2020, following a privacy impact assessment by the Ministry of Health, the national commission for the protection of personal data (the “Garante per la Protezione dei Dati Personali” or GPDP) gave a green light to use of the decentralized Immuni app,9 and two weeks later, the app was made available to the whole population.
France
The French government — following the advice of a dozen public expert bodies10 — opted for a centralized approach to collecting proximity data that did not rely on the GAEN system. On May 29, 2020, the French government issued an ad hoc decree to clarify the legal bases for the French DCT system11 and on June 2, 2020, made available an app called StopCovid.12 The decree specified the type of data being collected, the time-limits for data collection (limited to 6 months after the end of the emergency period) and how relevant principles of the GDPR were taken into account in the app’s design.
The French Government’s rationale for the centralized system was twofold. First, the government argued that the involvement of big tech companies with the decentralized approach (GAEN) is inappropriate as it undermines the prerogatives of the state in matters of public health protection. Second, the government argued that the centralized approach is more privacy-preserving because, rather than transmitting proximity data from one user’s phone to another’s, the StopCovid app sends each user’s data to the central server, whereas in the decentralized approach, this information was sent to all users’ smartphones.13
Switzerland
In other countries, policymakers amended existing data protection laws to create specific requirements regarding DCT in the context of the COVID-19 pandemic. Switzerland introduced new articles to its Epidemics Act of 2012 (818.101) to define the legal framework for DCT systems. Under Article 60 of the Epidemics Act, the Swiss Federal Office of Public Health already had authority over the collection and use of personal data — including contact information — for public health purposes. A federal law of June 19, 2020 (AS 2020 2191) introduced a provisional specific article (60a) to create a legal basis for the implementation of DCT in the country. The legislation stresses that individuals may voluntarily choose whether to use the national DCT app and prohibits enterprises and other private actors from either benefitting from or penalizing anyone for either participating or not participating in the national DCT system (art. 60a, 3). The legislation also specifies that data concerning users may only be stored on users’ mobile phones (art. 60a.5,b); that geolocation data may not be collected (art. 60a.5,c); that data be deleted as soon as they are no longer useful for contact-tracing purposes (art. 60a.5,d); and that the source code and all technical specifications of the system be made public (art. 60a.5, e). In parallel to these provisions, the Swiss Government issued specific guidance in the form of an ordinance defining basic operational procedures, as well as the procedures following a notification of an encounter with a positive case (818.101.25). The Swiss app, called SwissCovid, was launched on June 25, 2020.Reference Daniore14
Australia
In late April 2020, Australia released its DCT app called CovidSafe, which detected proximal contacts via Bluetooth. The Australian app was based on a system developed in Singapore that was made available as an open-source solution. Australia adopted a data protection approach to governing its DCT app, and in May 2020, the Australian Parliament enacted an amendment to the Privacy Act of 1998 to support the COVIDSafe app.Reference Goggin15 This Amendment introduced novel legal definitions related to DCT and extended privacy-related safeguards to data types and data collection activities specific to DCT. The Amendment also specified a number of data-related activities as serious criminal offences, including unauthorized data collection through DCT, unauthorized use or disclosure of COVID app-collected data; uploading data without consent, moving data collected through the app to locations outside of the country, decrypting encrypted data, and requiring participation in the DCT system by employers (94A). The amendments define app data as “personal information” and extend the authority of the data protection commissioner to allow assessments and investigations related to the app (94A).
United States
Unlike the other countries included in this study, the United States did not develop a nationwide DCT app and did not enact DCT-specific laws or regulations at the federal level. Instead, a number of state and local governments developed and released official DCT apps, sometimes with guidance from Apple and Google. By December 2020, twenty states, plus Puerto Rico and the District of Columbia, had released official GAEN apps, and as of July 2022, sixteen states were still using GAEN apps.16 In addition, three states released non-GAEN apps, described as “location diaries,” that collect and store location data on users’ phones, which data can then be voluntarily shared with a public health agency if the user subsequently tests positive.Reference Sato17 This state-by-state approach created gaps in coverage and a lack of interoperability across state borders.Reference Ramjee, Sanderson and Malek18
A number of existing federal privacy laws could apply to the use and dissemination of data collected through DCT apps, including laws related to data security, health information, labor and employment, consent, and anti-discrimination.Reference Kahn19 Constitutional privacy protections may also be relevant to DCT technology, particularly if information collected by DCT apps were accessible to law enforcement.Reference Rozenshtein20 But none of these federal laws reference digital contact tracing technology, and as of August 2022, none were updated in response to COVID-19.
Members of the U.S. Congress introduced four bills that would have created specific privacy protections for users of DCT apps,21 but as of November 2022, none of these bills has been passed by either chamber. A number of U.S. states enacted legislation regulating traditional contact tracing in response to COVID-19, but as of August 2022, only Kansas and Oregon had enacted a law that specifically restricts the collection and use of data collected digitally for contact-tracing purposes.22 The Kansas law itself is not expansive regarding DTC; it simply prohibits the use of cell phone location data for contact-tracing purposes.23 The Oregon law prohibits organizations from collecting, using, or disclosing personal health data without revokable, express consent from individuals, and specifies that such consent may not be obtained through a user interface that has been designed to trick users. Additionally, it specifies that contact tracing data cannot be used for commercial advertising or marketing algorithms. The legislatures in some other States, including California, Minnesota, New Jersey, New York, and Ohio, also introduced bills that would also regulate use of DCT apps, but none have become law.24
1.2 The Emergency Response Model
The remaining countries in our study adopted a very different approach to DCT governance, which we describe as the “Emergency Response Model.” The governments that adopted this model relied on emergency response laws in order to engage in larger-scale data collection than those that adopted the Data Protection Model. Rather than data minimization, the Emergency Response Model focuses on maximizing the public health benefits of DCT through the collection of vast quantities of personal location data stored in a centralized database accessible to the government.
South Korea
South Korea is a paradigmatic example of a country that authorized the development and use of DCT technology on the basis of emergency response laws. The South Korean government relied on its emergency response law to authorize a “network-based approach” to DCT that collects individual user data, including location data, directly from mobile phone networks (as well as other digital sources), and stores these data in a centralized database for ease of contact tracing and other public health interventions. South Korea’s DCT system was authorized under the Infectious Disease Control and Prevention Act (IDCPA), which provides for the Korean Center for Disease Control and Prevention (KCDC) to collect personal information necessary to control the spread of infectious diseases.25 Under this law, the government is authorized to collect personally identifiable network information about users directly from mobile network operators, including location data. The data collection authorized by the IDCPA falls within a standing public health emergency carve-out from South Korea’s typical digital privacy law.Reference Park and Cho26
On April 2, 2020, in response to COVID-19, the President Moon Jae-In relied on this law to issue an enforcement decree authorizing the collection and storage of additional personal data to track the spread of SARS-CoV-2.27 The presidential decree authorizes the collection of data including credit card data, transportation records, and image data captured from security cameras.28 In accordance with the IDCPA and the presidential decree, the South Korean government has collected information about persons who tested positive for SARS-CoV-2 as well as suspected close contacts directly from mobile network providers, banks, and other sources. Data collection was compulsory in the sense that data may be collected without the consent or even the active participation of the individual mobile phone user. Personalized information from these various sources was then collected and stored in a centralized government system called the Epidemic Investigation Support System (EISS). The Ministry of Health collected these data in a centralized database and used them to track the past movement of people who tested positive for COVID-19, using this information for contact tracing and as a basis for imposing quarantine.Reference Park29
Ghana
Similar to South Korea, Ghana utilized an emergency provision to authorize centralized network-based data collection in order to aid in the government’s contact-tracing efforts. On March 23, 2020, President Nana Addo Dankwa Akufo-Addo issued Executive Instrument 63 (E.I. 63), known as the Emergency Communications System Instrument, 2020, which requires mobile phone network operators and service providers to make available to the government information about mobile phone users, including cell-site location data and location logs, for the purposes of contact tracing.30 The president’s authority to issue E.I. 63 was based on Section 100 of the Electronic Communications Act (ECA) of 2008, which provides that “operators or providers of electronic communications networks or services” must, if required by an executive instrument, “provide any user information or otherwise [sic] in aid of law enforcement or national security.”31 The provision of network data by the government under E.I. 63 is compulsory and individual mobile phone users may not opt out of the government’s collection of their data from network operators.
On April 13, 2020, not long after the president issued E.I. 63, Vice President Dr. Mahamudu Bawumia announced the launch of an official contact-tracing app, GH COVID-19 Tracker, developed in collaboration with the Ministry of Communications (MoC).32 The app, which was subsequently updated and relaunched to expand its capabilities, incorporates geofencing and location data, together with QR code check-in functionality, to aid in contact tracing, identify COVID-19 “hotspots,” and manage event capacity in compliance with government-mandated guidelines and restrictions.33 Although downloading the app was voluntary, the app is only a secondary method of data-collection designed to accompany the mandatory collection of data directly from mobile phone network operators.
South Africa
South Africa provides another example of the Emergency Response Model. As in South Korea and Ghana, the initial authorization for DCT in South Africa was pandemic-response authority held by the executive branch. On March 18, 2020, the South African Minister of Cooperative Governance and Traditional Affairs issued COVID-specific regulations as authorized by Section 27(2) of the Disaster Management Act (57/2002). These regulations provide, among other things, that any government minister may “take any [] steps that may be necessary to prevent an escalation of the national state of disaster.”34 Pursuant to this provision, on April 4, 2020, the Information Regulator issued a “Guidance Note on the Processing Of Personal Information In The Management And Containment Of Covid-19 Pandemic,” in accordance with the Protection of Personal Information Act 4 of 2013 (POPIA).35 Among other things, this guidance document requires, under certain conditions, electronic communication service providers to provide the Government with mobile phone-based location data of individual users in order to “manage[] the spread of COVID-19.” (5.1)
On April 29, 2020, the Minister of Cooperative Governance and Traditional Affairs issued another set of regulations under the Disaster Management Act providing for the creation of a “COVID-19 Tracing Database,” a centralized system designed to collect and store personalized information about all individuals who have been tested for COVID-19 as well as known or suspected contacts of those who tested positive.36 These regulations and policy documents explicitly authorize the government to collect the location data of individuals who are known or reasonably suspected to have contracted COVID-19, and of the persons with whom they have been in contact, directly from any electronic service provider.37 The regulation strictly limits the use of these data to government contact-tracing purposes,38 but individuals have no opportunity to opt out of the collection or use of their data.39
Then, on September 2, 2020, the South African government released a new DCT app, called COVID Alert SA, based on the decentralized GAEN protocol.40 The new app was presented as privacy-preserving and as an effective way to protect public health in the course of the pandemic. Notably, however, this app supplemented — but did not replace or eliminate — the government’s ability to collect user data directly from mobile phone network operators and to store these data in the centralized COVID-19 Tracing Database.Reference Viljoen41
Israel
Finally, much like South Africa, Israel employed a two-pronged approach, including both a voluntary public-facing app and large-scale data collection directly from mobile phone networks. Israel provides a distinctive example of the Emergency Response Model, as Israel authorized its DCT under its national security law, as opposed to public health laws. Specifically, the more intrusive aspects of Israel’s DCT system were authorized under Sections 38 and 39 of the Basic Law of the Government of Israel, which grants far-reaching powers for declaring a state of emergency, including the temporary suspension of any existing statute.42
In March 2020, The Israeli Government issued Resolution 4916, which commissioned the Israeli Security Agency (ISA), Israel’s domestic security agency — also known as the Shin-Bet, “Shabak”, or General Security Service (GSS) — to collect data from mobile phones for digital contact tracing.43 The government expressed its commitment to limited data collection, including no recording of phone calls or text messages, and also promised to delete all information once the COVID-19 pandemic ended.Reference Shwartz Altshuler and Aridor Hershkovitz44 However, the technology deployed by the ISA, the SIGINT Oversight system also known as “the Tool,” collected personal cell-site location data based on mobile phone caches, which was then cross-referenced with the locations of individuals who tested positive for COVID-19.45 This personalized location information allowed the ISA to identify the names and contact information of individuals who were in the same location as those who tested positive during likely periods of transmissibility. The Ministry of Health could then use this information to contact people who may have been exposed to the coronavirus, often requiring them to quarantine and register with the Ministry of Health’s database.46 The Ministry of Health also released a downloadable app, called HaMagen, to facilitate its communication process.47 As in South Africa, however, this app augmented, but did not replace, the government’s compulsory centralized data collection process.
2. Discussion
As described above, our research revealed a stark dichotomy between two key DCT governance models adopted by the countries included in our survey. (See Table 2.) The countries that prioritized individual privacy in adopting their DCT systems — namely, Italy, France, Australia, and Switzerland — adhered to principles of data minimization and privacy by design.Reference Bygrave48 These countries adopted legislative interventions specifically aimed at linking DCT to privacy and data protection provisions and created strict limits on data collection, storage, and analysis for DCT purposes (privacy-by-default). Moreover, all of these countries embedded technological safeguards such as anonymization and data-minimization in their DCT systems — e.g. the collection of Bluetooth proximity data, not location data (privacy-by-design). Finally, in all of these countries, DCT was app-based and the use of DCT was voluntary, with digital monitoring limited to those who chose to download and install the app onto their phone.
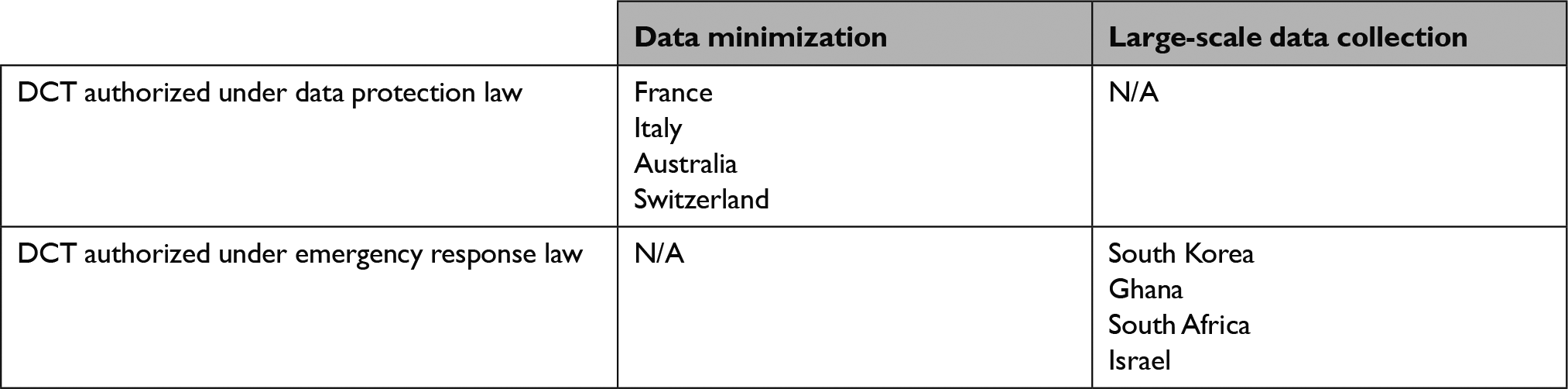
On the other hand, the countries that authorized their DCT systems under emergency response laws — namely, South Korea, Ghana, South Africa, and Israel — allowed for the collection of users’ location data directly from mobile phone network operators, without requiring the consent or cooperation of users.
Both models of DCT governance are premised on the assumption that widespread adoption of DCT can substantially boost virus containment efforts (in conjunction with other measures). Given the importance of boosting uptake, we believe that a number of important lessons can be learned about the governance of digital technologies for public health based on these contrasting governance approaches to DCT technology during the first year of the COVID-19 pandemic.
2.1 The Data Protection Model Emphasizes Individual Risk Over Collective Benefit
The Data Protection Model attributes a pivotal role to protecting user privacy, and advocates of this model assert that increasing use of DCT is largely a function of addressing legitimate privacy concerns on the part of the population. However, although the Data Protection Model was intended to address privacy concerns and thus to drive widespread uptake of DCT systems among citizens, the actual level of uptake of such systems failed to meet expectations and was insufficient to generate its intended public health impact. For this reason, although emerging studies continue to demonstrate the impact of DTC in the pandemic, the effort to use DCT apps governed by the Data Protection Model has been publicly perceived as a failure, especially in Europe.49
In many countries that employed the Data Protection Model, privacy-related risks have been at the forefront of the public debate about DCT. Studies have shown that the media’s emphasis on privacy concerns — coupled with uncertainty about the effectiveness of DCT — may have materially undermined public trust and interest in the new technology. For example, an analysis of newspaper coverage of DCT apps in Germany, Austria, and Switzerland suggests that an emphasis on “debates surrounding data protection, privacy, and voluntariness” together with characterizing the use of DCT as controversial, may have caused members of the public to be reluctant and cautious about using DCT.Reference Amann, Sleigh and Vayena50 Similarly, in the United States, polling shows that State governments considered privacy risks to be a barrier to implementing the new app-based or mobile phone-based technology to respond to the pandemic.Reference Van Ness51
It is possible that individuals therefore reacted to the adoption of the Data Protection Model by seeing it as a reason to avoid using DCT, not an assurance of its safety. Individuals have grown increasingly wary of digital technology’s capacity to collect personal data without their knowledge or consent. And a legislative approach focused on data protection in the context of data-collection technology generally signals the potential privacy risks of such technology. Lending credence to these concerns, it was reported that the Australian national intelligence agency was able to access data collected by its national DCT app, despite comprehensive legal protections intended in part to prevent this from happening.52
In addition, individuals may have been wary of the central role that private companies, especially Apple and Google, played in DCT development and governance. Largely because of the need for rapid DCT deployment, some countries, such as Italy and the United States, relied on private sector providers for both the API and the actual development of their DCT apps. France, by contrast, developed its DCT app in-house, in order to avoid relying on the GAEN system.Reference Dillet53 In addition, some scholars have suggested that Google and Apple sought self-interested while at the same time presenting themselves as more credible “champions of privacy than some democratic governments.”Reference Sharon54 It is clear that these companies stepped in at an early stage to design a DCT system that protects the privacy of the app users by limiting the types and uses of data collected, sometimes at the cost of public health utility.Reference Fahey and Hino55 In the UK for instance, Apple and Google prevented an update of the NHS DCT app that would have enabled users to be notified in case their log of locations (generated as they check-in in venues by scanning QR codes with the app) matched a list of venues considered as potential virus hotspots.Reference Hern56 Moreover, researchers involved with the development of the NHS app have argued that an ability to evaluate the effectiveness of DCT systems is essential to their application going forward, necessitating the collection of data, including location data, that is not allowed by the GAEN system.Reference Colizza57
Arguably, the influence exerted by Apple and Google undermined the benefits of DCT for public health protection. Given the ongoing international debate about the excessive power accumulated by unaccountable tech giants, it is not surprising that governments’ reliance on Google and Apple in a matter of public interest and common concern may have alienated at least some potential DCT users. This effect should not be attributed to the lack of public trust in corporations such as Apple and Google.Reference Newton58 Rather, the delegation of governance prerogatives to tech giants may have reinforced currents of public distrust in the capacity of governments to adequately handle the response to the COVID-19 emergency, specifically as to the use of novel digital health solutions.Reference Altmann59 The reliance on public/private partnerships should be evaluated to protect against loss of public trust and engagement in a DCT effort.
It appears that the public health purpose for using DCT was eclipsed in many countries by the Data Protection Model’s emphasis on individual privacy. Empirical studies have shown that members of the public cite lack of perceived benefit as the main reason for not using DCT apps,Reference Von Wyl60 which in turn is reflected in a widespread media discussion of such systems having unclear benefit. In a pandemic, another message may therefore need to be communicated along with the information-protection message of the Data Protection Model. Individuals may be willing to take on sacrifices or inconveniences to help out their community in responding to a pandemic. This claim is supported by empirical studies showing that while privacy concerns nurture skepticism towards the use of DCT, the prospect of contributing to the “greater good” motivates people to embrace such use.Reference Williams61 Indeed, extensive surveys conducted in Europe suggest that even those who value privacy are also motivated by a variety of values in this context, including protecting the health of their community. This suggests that DCT might have gained greater public acceptance if it had been more clearly presented as a public health intervention whose use would allow individuals to contribute to fighting the pandemic.
In employing the Data Protection Model of governance, many European governments, almost certainly influenced by the GDPR, may have failed to tap into their citizens’ motivations to help protect the health of their fellows and their community by accepting fewer privacy protections.Reference Jennings, Dawson and Verweij62 Rather than creating governance mechanisms to build public trust and transparency about the functionality and potential benefits of the DCT apps, those governments focused on privacy safeguards such as data-minimization. At least arguably, this limited the public-health utility of DCT by reducing the quantity and types of valuable data to which public health officials had access. For example, the GAEN approach, employed in the United States and in much of Europe, collects only anonymized proximity data, stored in decentralized fashion on users’ phones. In contrast, the use of less privacy-preserving approaches, such as collecting location or proximity data in a centralized database to which public health authorities have access, enables a more granular tracking of positive cases.
Effective governance of DCT will likely require a public justification based on the potential benefit to the community of widespread adoption of the technology. Even if other forms of public justification are employed — e.g., direct communication from the public health agencies — a narrow focus on individual privacy protection is arguably incompatible with the public health value of DCT. DCT requires a governance approach that builds public trust, premised on adequate safeguards, dedicated oversight bodies to deter data misuse on the part of both private-sector actors and governments,Reference Blasimme, Ferretti and Vayena63 and transparency about evidence-based objectives and the expected contribution of the technology to combatting a public health emergency like the COVID-19 pandemic.Reference Blasimme and Vayena64
To summarize, the Data Protection Model has a number of limitations when applied to DCT governance. Most importantly, its prioritization of user privacy tends to limit data collection, as well as data analysis, sharing, and use, and so may reduce the public health utility of DCT. And ironically, by emphasizing privacy as a concern, the Data Protection model may undermine or conflict with the government’s efforts to motivate uptake of DCT. Ideally, a governance approach that is well suited to DCT should be able to determine the appropriate privacy protections in light of public values, democratic deliberation, and changing facts on the ground, and to communicate the potential of DCT to protect human life in a widespread pandemic.
2.2 The Emergency Response Model Raises Concerns about Excessive Government Surveillance
In contrast with the Data Protection Model, the Emergency Response Model allowed governments to prioritize the collection of data for public health purposes over protecting the privacy of user data. For example, research suggests that South Korea’s comprehensive network-based DCT system may have helped to limit the spread of SARS-CoV-2.Reference Huang, Sun and Sui65 Similarly, Ghana’s contact tracing system (which includes both digital and traditional data collection), together with its significant testing capacity, may have contributed to the country’s promising public health outcomes.Reference Zhang, Nonvignon and Mao66
Authorizing DCT technology under emergency response powers, however, raises significant concerns about government surveillance and unchecked governmental authority. In particular, the collection of personal information necessary for effective DCT raises serious risks of government misuse of data and invasion of privacy. In South Korea, for example, concerns were raised by scholars and civil rights groups that the government has overused this system to collect information pertaining to more individuals than strictly necessary to respond effectively to the pandemic, and that, in particular, the government’s large-scale data collection techniques violated constitutional rights protections.Reference Jung, Lee, Kim and Lee67
In Israel, human rights groups brought legal challenges against the government’s DCT surveillance system, resulting in the Israeli Supreme Court overturning the initial emergency justification of DCT and requiring legislative approval.Reference Keshet68 In light of these challenges, and citing the lack of parliamentary oversight and disproportionate infringement on the right to privacy, the Israeli government decided to repeal the emergency orders, switching the foundation of ISA surveillance powers to the ISA Security Law.69 However, the Supreme Court later held this interpretation of the ISA Security Law to be illegal, ruling that involving the ISA in COVID-19-response measures would require legislative efforts.70 Shortly after, in July, 2020, the Knesset enacted a law authorizing the ISA to collect identifiable mobile phone data from individuals who have tested positive for Sars-CoV-2, and to provide the Ministry of Health with their location data and the identity of their close contacts.71
The contrasting governance approaches adopted for “first generation” DCT can teach us important lessons about the future governance of DCT. We must learn from both governance models — Data Protection and Emergency Response — in order to develop a new governance approach that is able to guide the ethical and effective use of DCT and related digital public health technology going forward. Ultimately, the effective governance of DCT may help end the COVID-19 pandemic and to prepare for and combat potential infectious disease outbreaks in the future.
In Ghana, a number of scholars argued that President Akufo-Addo exploited the COVID-19 crisis to bolster his power at the expense of transparency, accountability, and civil rights.72 Some legal scholars argued that because E.I. 63 authorizes the collection of network-based data of all mobile phone users, it raises significant concerns about invasion of privacy and abuse of power and may be inconsistent with the spirit of Section 100 of the ECA.73 Others argued that E.I. 63 is unconstitutional on the ground that the president has not declared an official State of Emergency, as provided under articles 31 and 32 of the 1992 Constitution, as well as the Emergency Powers Act 1994 (Act 472).Reference Addadzi-Koom74 Declaring an official State of Emergency would provide a sound constitutional basis for many of President Akufo-Addo’s pandemic-response policies, but would also subject them to the oversight of Parliament and other governmental bodies.75 Instead of declaring a State of Emergency, the president imposed restrictions and other pandemic responses under the recently enacted Imposition of Restrictions Act, which has also prompted significant criticism from legal scholars and civil rights advocates.76
Responding to these concerns, some have argued that, in countries such as South Korea, public acceptance of DCT was largely due to the government’s concerted communications about the expected public benefits of the technology.Reference Mello and Wang77 It is difficult to verify public acceptance of a compulsory network-based surveillance system that left no opportunity for citizens to opt-out. It does seem, however, that the South Korean public was aligned with the government’s public health goals; the fact that certain measures are mandatory does not rule out that they are voluntarily supported by public trust, as in the case of mandatory use of seatbelts, for instance.
The collection by the government of enormous amounts of personal data via mobile phones, as occurred in the countries that adopted the Emergency Response Model, is a risk that must be evaluated in context. Emergency response authority may be an effective tool for responding to a pandemic situation. Governments must act fast, and flexibly, to respond to a rapidly changing public health crisis, and formal procedures of law and policy-making are sometimes inadequate to that task. It would, therefore, be misguided to criticize all forms of emergency response just because they do not employ traditional mechanisms of oversight, accountability, and public participation. However, the legitimacy of the use of exceptional state powers in the context of the exceptional circumstances of the COVID-19 pandemic has been a matter of significant debate, and the government’s collection and use of personal data collected via mobile phones, raises novel ethical questions, even where the goal is the protection of public health.
In short, authorizing DCT under an Emergency Response governance model risks excessive government surveillance and the infringement of civil liberties. Without adequate oversight safeguards, DCT technology may be used by the government to collect extensive amounts of personally identifiable data, raising fears about intrusive forms of surveillance that could extend beyond public health necessities.
Conclusion
Our research shows that in the countries surveyed, DCT systems were accompanied by one of two distinct models of governance, each of which has critical limitations. First, the Data Protection Model was not ideally suited to digital public health interventions such as DCT, because it tended to prioritize user privacy in a situation where, unlike commercial transactions, human lives are at stake. By emphasizing privacy concerns rather than the critical need to collect personal data to prevent widespread infection, the Data Protection Model may have undermined uptake of DCT. The Emergency Response Model, on the other hand, often lacked adequate oversight, accountability, and privacy protections. Although this approach may promise greater public health utility, especially if it involves a more data-intensive DCT system, it raises serious questions of legitimacy and justification absent an adequate governance and oversight infrastructure.
Effective and ethical use of DCT going forward requires incorporation of traditional governance values, including accountability, transparency, and public participation. The emergency context should not prompt governments to abandon these values; but at the same time, these values cannot be adequately realized (or replaced) by special features of the design of the technology itself.
A new governance approach is arguably required for designing and implementing DCT technology going forward. Much like traditional contact tracing, DCT must be explained and “marketed” to individuals in terms of civic responsibility, solidarity, and collective action. This objective can be achieved through transparent governance, enabling the public to know what impact governments expect DCT to have in containing the spread of the virus, and what levels of individual participation, including personal data-sharing, would be required to meet those expectations.
The contrasting governance approaches adopted for “first generation” DCT can teach us important lessons about the future governance of DCT. We must learn from both governance models — Data Protection and Emergency Response — in order to develop a new governance approach that is able to guide the ethical and effective use of DCT and related digital public health technology going forward. Ultimately, the effective governance of DCT may help end the COVID-19 pandemic and to prepare for and combat potential infectious disease outbreaks in the future.
Note
The study described in this article was commissioned and partly funded by the World Health Organization (WHO). Copyright in the original work on which this article is based belongs to WHO. The authors have been given permission to publish this article. The authors alone are responsible for the views expressed in this publication and they do not necessarily represent the views, decisions or policies of the WHO. Additional funding was provided by the Swiss National Science Foundation (NRP77 grant 407740_1873560). BH reports support from the Hecht-Levi Postdoctoral Fellowship. RGA reports support from the Oxford-Johns Hopkins Global Infectious Disease Collaborative, funded by the Wellcome Trust (grants numbers 221719 and 216355), and partial support from the Zuckerman-CHE STEM Leadership Program. Additional research support was provided by Arnold & Porter Kaye Scholer LLP, and by Shannon Hubbs, Antonis Kouris, and Renan Leonel at ETH. Dr. Vayena reports grants from the Swiss National Science Foundation, during the conduct of the study; personal fees from IQVIA, personal fees from Roche Diagnostics, outside the submitted work; and service as Chair of the Greek National Bioethics and Technoethics Committee. Ms. Perkins reports grant funding from Google, outside the submitted work.




