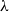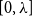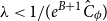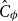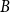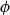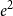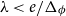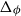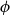1. Introduction
Gibbs point processes are a fundamental model of random spatial phenomena in the continuum. Most classically, such processes are used to model a gas under local interactions (see Ruelle’s [Reference Ruelle31] text). Beyond that, Gibbs point processes are used to model various physical phenomena that often exhibit local repulsion, such as the locations of galaxies in the universe, the time and place of earthquakes, and the growth of trees in a forest; see [Reference Daley and Vere-Jones5, Reference Møller and Waagepetersen22] for these applications and more. A simple and well-studied example of a Gibbs point process is the hard-sphere model, where one samples a Poisson point process in a set of finite volume in
![]() $\mathbb{R}^d$
and conditions on no two points having distance less than some parameter
$\mathbb{R}^d$
and conditions on no two points having distance less than some parameter
![]() $r \gt 0$
. In order to better understand these models one often wants to approximately compute the partition function of the model, which may be understood as a weighted count of allowable configurations of points. The partition function grows exponentially in the volume, making exact computation intractable even for basic examples. Additionally, the rate of exponential growth is equal to the infinite-volume pressure, a central quantity in statistical physics.
$r \gt 0$
. In order to better understand these models one often wants to approximately compute the partition function of the model, which may be understood as a weighted count of allowable configurations of points. The partition function grows exponentially in the volume, making exact computation intractable even for basic examples. Additionally, the rate of exponential growth is equal to the infinite-volume pressure, a central quantity in statistical physics.
Approximating the partition function and sampling – either approximately or exactly – are the two main algorithmic problems associated with Gibbs point processes. Under very mild assumptions, polynomial-time approximate sampling of the point process can be used to provide a randomised approximation to the partition function. Many techniques have been applied to Gibbs point processes for approximate and exact sampling in certain regimes; in fact, the seminal Metropolis-Hastings algorithm was developed to sample from the hard-sphere model in dimension 2 [Reference Metropolis, Rosenbluth, Rosenbluth, Teller and Teller21].
On the other hand, deterministic approximation algorithms for partition functions of Gibbs point processes are less well-understood. For Gibbs point processes, to our knowledge the only rigorous result giving a deterministic algorithm is that of Friedrich, Göbel, Katzmann, Krejca and Pappik [Reference Friedrich, Göbel, Katzmann, Krejca and Pappik6], which shows that for the special case of hard spheres, one may approximate the partition function in quasipolynomial time for a certain range of parameters. The authors show that the hard-sphere model can be well approximated by its discrete analogue (the hard-core model) allowing them to apply known algorithmic results from the discrete setting (see Section 1.3 for more detail).
In this paper, we provide a quasipolynomial-time deterministic approximation algorithm for the partition function for a general class of stable Gibbs point processes. Our main result is stated only under the assumption of zero-freeness of the partition function; from there, we deduce two main corollaries using existing zero-freeness results from the literature, one which applies to all stable potentials and a stronger result that applies to the more restricted class of repulsive potentials. We defer formal statements to Section 1.2.
Our approach is via Barvinok’s interpolation method [Reference Barvinok2] combined with use of the cluster expansion for Gibbs point processes. This allows us to work with the Gibbs process directly, rather than a discrete approximation of the process. By combining our result with the zero-free region for stable potentials guaranteed by the cluster expansion, we obtain what appears to be the first algorithmic result for stable, non-repulsive potentials. In the special case of a repulsive potential, combining our result with previous work of the second author and Perkins on zero-freeness [Reference Michelen and Perkins19] yields the first quasipolynomial-time deterministic approximation algorithm for a large class of repulsive potentials (which includes the hard-sphere model) and range of parameters. For the hard-sphere potential
![]() $\phi$
, we note that [Reference Michelen and Perkins19, Lemma 12] gives an explicit bound of
$\phi$
, we note that [Reference Michelen and Perkins19, Lemma 12] gives an explicit bound of
![]() $\Delta _\phi \lt C_\phi (1 - 8^{-d-1})$
where
$\Delta _\phi \lt C_\phi (1 - 8^{-d-1})$
where
![]() $\Delta _\phi, C_\phi$
denote the potential-weighted connective constant and temperedness constant of
$\Delta _\phi, C_\phi$
denote the potential-weighted connective constant and temperedness constant of
![]() $\phi$
, respectively (defined in the next sections). This demonstrates that our algorithm works for a wider range of parameters than the previous deterministic algorithms [Reference Friedrich, Göbel, Katzmann, Krejca and Pappik6]. Additionally, [Reference Friedrich, Göbel, Krejca and Pappik7] argues that the connective constant of the discretization used in [Reference Friedrich, Göbel, Katzmann, Krejca and Pappik6, Reference Friedrich, Göbel, Krejca and Pappik7] would not provide an improvement to their results; as such, working in the continuum and using the zero-freeness result of [Reference Michelen and Perkins19] gets around this issue.
$\phi$
, respectively (defined in the next sections). This demonstrates that our algorithm works for a wider range of parameters than the previous deterministic algorithms [Reference Friedrich, Göbel, Katzmann, Krejca and Pappik6]. Additionally, [Reference Friedrich, Göbel, Krejca and Pappik7] argues that the connective constant of the discretization used in [Reference Friedrich, Göbel, Katzmann, Krejca and Pappik6, Reference Friedrich, Göbel, Krejca and Pappik7] would not provide an improvement to their results; as such, working in the continuum and using the zero-freeness result of [Reference Michelen and Perkins19] gets around this issue.
1.1. Formal definition of the model
The point processes we consider are defined by three parameters:
-
a measurable set
 $S \subset \mathbb{R}^d$
of finite volume,
$S \subset \mathbb{R}^d$
of finite volume, -
a parameter
 $\lambda \geqslant 0$
referred to as the activity or fugacity,
$\lambda \geqslant 0$
referred to as the activity or fugacity, -
a pair potential
 $\phi \;:\;\mathbb{R}^d \to \mathbb{R} \cup \{+ \infty \}$
satisfying
$\phi \;:\;\mathbb{R}^d \to \mathbb{R} \cup \{+ \infty \}$
satisfying
 $\phi (x) = \phi (\!-\!x)$
.
$\phi (x) = \phi (\!-\!x)$
.
The temperedness constant of a potential is defined as
The temperedness constant may be understood as a measure of the strength of the potential. We say that a potential
![]() $\phi$
is tempered if
$\phi$
is tempered if
![]() $C_\phi \lt \infty$
, and always assume that
$C_\phi \lt \infty$
, and always assume that
![]() $\phi$
is tempered. The energy of a configuration of points
$\phi$
is tempered. The energy of a configuration of points
![]() $\{x_1,\ldots,x_{N}\} \subset \mathbb{R}^d$
is defined by
$\{x_1,\ldots,x_{N}\} \subset \mathbb{R}^d$
is defined by
We will always assume that
![]() $\phi$
is stable, meaning that there is a constant
$\phi$
is stable, meaning that there is a constant
![]() $B \geqslant 0$
so that for all
$B \geqslant 0$
so that for all
![]() $N$
and
$N$
and
![]() $x_1,\ldots,x_N$
we have
$x_1,\ldots,x_N$
we have
The infimum over such
![]() $B$
is called the stability constant of
$B$
is called the stability constant of
![]() $\phi$
. The assumption of stability is used to show that the partition function – and thus the Gibbs point process – itself is well-defined. Under certain conditions on
$\phi$
. The assumption of stability is used to show that the partition function – and thus the Gibbs point process – itself is well-defined. Under certain conditions on
![]() $\phi$
, the assumption of stability is a necessary condition for the point process to be well-defined (see [Reference Ruelle31, Section 3.2] for a detailed discussion and many examples). A potential
$\phi$
, the assumption of stability is a necessary condition for the point process to be well-defined (see [Reference Ruelle31, Section 3.2] for a detailed discussion and many examples). A potential
![]() $\phi$
is repulsive if
$\phi$
is repulsive if
![]() $\phi (x) \geqslant 0$
for all
$\phi (x) \geqslant 0$
for all
![]() $x$
. In particular, repulsive potentials are stable with stability constant
$x$
. In particular, repulsive potentials are stable with stability constant
![]() $B = 0$
.
$B = 0$
.
The Gibbs point process in
![]() $S$
with potential
$S$
with potential
![]() $\phi$
at activity
$\phi$
at activity
![]() $\lambda$
is the point process in
$\lambda$
is the point process in
![]() $S$
whose density against the Poisson point process of activity
$S$
whose density against the Poisson point process of activity
![]() $\lambda$
is proportional to
$\lambda$
is proportional to
![]() $e^{-H(x_1,\ldots,x_N)}$
. The grand canonical partition function at activity
$e^{-H(x_1,\ldots,x_N)}$
. The grand canonical partition function at activity
![]() $\lambda$
is defined by
$\lambda$
is defined by
 \begin{equation} Z_S(\lambda ) = \sum _{ k \geqslant 0} \frac{\lambda ^k}{k!} \int _{S^k} e^{-H(x_1,\ldots,x_k)}\,dx_1\,\ldots \,dx_k. \end{equation}
\begin{equation} Z_S(\lambda ) = \sum _{ k \geqslant 0} \frac{\lambda ^k}{k!} \int _{S^k} e^{-H(x_1,\ldots,x_k)}\,dx_1\,\ldots \,dx_k. \end{equation}
Throughout, we work with the case of
![]() $S = \Lambda _n\;:\!=\; [\!-\!n,n]^d \subset \mathbb{R}^d$
, i.e. the axis parallel box of side-length
$S = \Lambda _n\;:\!=\; [\!-\!n,n]^d \subset \mathbb{R}^d$
, i.e. the axis parallel box of side-length
![]() $2n$
. One of the most studied examples of a Gibbs point process is the hard-sphere model, which is defined by the potential
$2n$
. One of the most studied examples of a Gibbs point process is the hard-sphere model, which is defined by the potential
 \begin{align} \phi (x)= \begin{cases} +\infty & \textrm{if}\, \|x\|_2 \lt r \\[5pt] 0 & \textrm{otherwise}, \end{cases} \end{align}
\begin{align} \phi (x)= \begin{cases} +\infty & \textrm{if}\, \|x\|_2 \lt r \\[5pt] 0 & \textrm{otherwise}, \end{cases} \end{align}
for fixed
![]() $r\gt 0$
. The hard-sphere model is supported on configurations
$r\gt 0$
. The hard-sphere model is supported on configurations
![]() $\{x_1,\ldots,x_{N}\}$
such that
$\{x_1,\ldots,x_{N}\}$
such that
![]() $H(x_1,\ldots,x_N) =0$
i.e. configurations consisting of the centres of a packing of spheres of radius
$H(x_1,\ldots,x_N) =0$
i.e. configurations consisting of the centres of a packing of spheres of radius
![]() $r/2$
.
$r/2$
.
Another similar example is the Strauss potential, in which the
![]() $+\infty$
in the definition of the hard-sphere potential is replaced with a parameter
$+\infty$
in the definition of the hard-sphere potential is replaced with a parameter
![]() $a \gt 0$
.
$a \gt 0$
.
Among the most common examples of a stable potential that is not repulsive is a Lennard-Jones potential (see [Reference Ruelle31, Section 3.2.10]). While there are many examples of potentials that are called Lennard-Jones potentials, they are characterised by being strongly repulsive at short distances and weakly attractive at far distances. A large family of widely used potentials is of the form
for parameters
![]() $A,B \gt 0$
and
$A,B \gt 0$
and
![]() $\alpha \gt d$
, where we recall
$\alpha \gt d$
, where we recall
![]() $d$
is the underlying dimension. One may also truncate this potential to be of finite range by simply setting it equal to
$d$
is the underlying dimension. One may also truncate this potential to be of finite range by simply setting it equal to
![]() $0$
if
$0$
if
![]() $\|x\|_2 \geqslant T$
for some parameter
$\|x\|_2 \geqslant T$
for some parameter
![]() $T$
, and this still yields a stable potential.
$T$
, and this still yields a stable potential.
1.2. Statement of results
Our results will require only two additional assumptions on the potential: first a basic assumption on its form so that we may approximately compute certain volumes; and second a zero-freeness assumption. The zero-freeness assumption we use for stable (non-repulsive) potentials is a classical result that follows from the cluster expansion [Reference Procacci and Yuhjtman28, Reference Ruelle31], while in the repulsive case, we will use the work of the second author and Perkins [Reference Michelen and Perkins19]. We begin with the assumption required for computational purposes.
Assumption 1.1.
There are compact centrally symmetric convex sets
![]() $\{0\} = K_0 \subset K_1 \subset K_2 \subset \ldots \subset K_\ell$
so that the function
$\{0\} = K_0 \subset K_1 \subset K_2 \subset \ldots \subset K_\ell$
so that the function
![]() $x\mapsto \exp\!(\!-\!\phi (x))$
is
$x\mapsto \exp\!(\!-\!\phi (x))$
is
![]() $L$
-Lipschitz on each of
$L$
-Lipschitz on each of
![]() $\Delta _j\;:\!=\; K_{j} \setminus K_{j-1}$
. Additionally assume that there is an
$\Delta _j\;:\!=\; K_{j} \setminus K_{j-1}$
. Additionally assume that there is an
![]() $R\gt 0$
so that
$R\gt 0$
so that
![]() $\mathrm{supp}(\phi ) \subset K_\ell \subset [\!-\!R,R]^d$
and
$\mathrm{supp}(\phi ) \subset K_\ell \subset [\!-\!R,R]^d$
and
![]() $[\!-\!1/R,1/R]^d \subset K_1$
. We work in a real-valued model of computation, and assume unit cost for elementary operations; we also assume that evaluation of
$[\!-\!1/R,1/R]^d \subset K_1$
. We work in a real-valued model of computation, and assume unit cost for elementary operations; we also assume that evaluation of
![]() $e^{-\phi }$
as well as checking if a point lies in a given
$e^{-\phi }$
as well as checking if a point lies in a given
![]() $K_j$
have unit cost.
$K_j$
have unit cost.
Assumption 1.1 essentially has two elements: it assumes that the potential
![]() $\phi$
has a certain amount of (piecewise) regularity, and also assumes that
$\phi$
has a certain amount of (piecewise) regularity, and also assumes that
![]() $\phi$
is of finite range. We are not aware of any natural potential
$\phi$
is of finite range. We are not aware of any natural potential
![]() $\phi$
in the literature that fails to satisfy the piecewise regularity portion of the assumption. There are however many natural potentials that are not of finite range.
$\phi$
in the literature that fails to satisfy the piecewise regularity portion of the assumption. There are however many natural potentials that are not of finite range.
We remark that the hard-sphere potential (5), the Strauss potential, and the truncated Lennard-Jones potential are easily seen to satisfy Assumption 1.1.
1.2.1. A note on asymptotic notation
Throughout the paper, we think of the parameters
![]() $d, \ell, L$
, and
$d, \ell, L$
, and
![]() $R$
from Assumption 1.1 as fixed and allow the implicit constants in our asymptotic notation to depend on these parameters.
$R$
from Assumption 1.1 as fixed and allow the implicit constants in our asymptotic notation to depend on these parameters.
Our main theorem is that we obtain deterministic approximation algorithms for
![]() $Z_S(\lambda )$
for potentials satisfying Assumption 1.1 and the following zero-freeness assumption on
$Z_S(\lambda )$
for potentials satisfying Assumption 1.1 and the following zero-freeness assumption on
![]() $Z_S(\lambda )$
.
$Z_S(\lambda )$
.
Assumption 1.2.
We say a stable potential
![]() $\phi$
satisfies Assumption 1.2 at
$\phi$
satisfies Assumption 1.2 at
![]() $\lambda _0 \gt 0$
if there exist constants
$\lambda _0 \gt 0$
if there exist constants
![]() $\delta, C \gt 0$
so that the following holds. For all bounded, measurable
$\delta, C \gt 0$
so that the following holds. For all bounded, measurable
![]() $S \subset \mathbb{R}^d$
we have
$S \subset \mathbb{R}^d$
we have
where
Assumption 1.2 may be understood as saying that the Gibbs point process exhibits no phase transition in the regime
![]() $[0,\lambda _0]$
in the Lee-Yang sense (see Section 1.3).
$[0,\lambda _0]$
in the Lee-Yang sense (see Section 1.3).
Given a number
![]() $Z$
, an
$Z$
, an
![]() $\varepsilon$
-approximation to
$\varepsilon$
-approximation to
![]() $Z$
is a value
$Z$
is a value
![]() $\hat{Z}$
so that
$\hat{Z}$
so that
![]() $e^{-\varepsilon }\hat{Z} \leqslant Z \leqslant e^{\varepsilon } \hat{Z}$
. Our main theorem asserts a quasipolynomial-time approximation for the partition function under these two assumptions. Recall that
$e^{-\varepsilon }\hat{Z} \leqslant Z \leqslant e^{\varepsilon } \hat{Z}$
. Our main theorem asserts a quasipolynomial-time approximation for the partition function under these two assumptions. Recall that
![]() $\Lambda _n\;:\!=\; [\!-\!n,n]^d \subset \mathbb{R}^d$
.
$\Lambda _n\;:\!=\; [\!-\!n,n]^d \subset \mathbb{R}^d$
.
Theorem 1.3.
Let
![]() $\phi$
be a stable pair potential that satisfies the regularity Assumption 1.1. Suppose
$\phi$
be a stable pair potential that satisfies the regularity Assumption 1.1. Suppose
![]() $\phi$
satisfies the zero-freeness Assumption 1.2 at
$\phi$
satisfies the zero-freeness Assumption 1.2 at
![]() $\lambda \geqslant 0$
. Let
$\lambda \geqslant 0$
. Let
![]() $\varepsilon \in (0,1)$
,
$\varepsilon \in (0,1)$
,
![]() $n\in \mathbb{N}$
. Then there is a deterministic algorithm to compute an
$n\in \mathbb{N}$
. Then there is a deterministic algorithm to compute an
![]() $\varepsilon$
-approximation to
$\varepsilon$
-approximation to
![]() $Z_{\Lambda _n}(\lambda )$
with runtime at most
$Z_{\Lambda _n}(\lambda )$
with runtime at most
![]() $\exp\!(O(\log ^3(|\Lambda _n|/\varepsilon )))$
.
$\exp\!(O(\log ^3(|\Lambda _n|/\varepsilon )))$
.
We note that the implicit constant in the exponent depends on the potential
![]() $\phi$
as well as the activity
$\phi$
as well as the activity
![]() $\lambda$
.
$\lambda$
.
We will deduce two main corollaries from Theorem 1.3. The first of which deduces an algorithm for all stable potentials in the regime of cluster expansion convergence. The fact that for
![]() $\lambda \lt (e^{1+2B} C_\phi )^{-1}$
a stable potential
$\lambda \lt (e^{1+2B} C_\phi )^{-1}$
a stable potential
![]() $\phi$
satisfies Assumption 1.2 is a direct consequence of the cluster expansion (see, e.g., (11) or [Reference Ruelle31, Thm 4.2.3]). This classical result was recently improved by Procacci and Yuhjtman [Reference Procacci and Yuhjtman28] who showed that any stable tempered potential
$\phi$
satisfies Assumption 1.2 is a direct consequence of the cluster expansion (see, e.g., (11) or [Reference Ruelle31, Thm 4.2.3]). This classical result was recently improved by Procacci and Yuhjtman [Reference Procacci and Yuhjtman28] who showed that any stable tempered potential
![]() $\phi$
satisfies Assumption 1.2 at all
$\phi$
satisfies Assumption 1.2 at all
![]() $\lambda \lt (e^{1+B} \hat C_\phi )^{-1}$
, where
$\lambda \lt (e^{1+B} \hat C_\phi )^{-1}$
, where
We note that
![]() $\hat C_\phi \leqslant C_\phi$
for all
$\hat C_\phi \leqslant C_\phi$
for all
![]() $\phi$
with equality if
$\phi$
with equality if
![]() $\phi$
is repulsive.
$\phi$
is repulsive.
Corollary 1.4.
Let
![]() $\phi$
be a stable tempered potential satisfying Assumption 1.1, let
$\phi$
be a stable tempered potential satisfying Assumption 1.1, let
![]() $B$
denote its stability constant and let
$B$
denote its stability constant and let
![]() $\hat C_\phi$
be as in (7). Let
$\hat C_\phi$
be as in (7). Let
![]() $\varepsilon \in (0,1)$
,
$\varepsilon \in (0,1)$
,
![]() $n\in \mathbb{N}$
. Then for all
$n\in \mathbb{N}$
. Then for all
![]() $\lambda \lt (e^{1+B} \hat C_\phi )^{-1}$
, there is a deterministic algorithm to compute an
$\lambda \lt (e^{1+B} \hat C_\phi )^{-1}$
, there is a deterministic algorithm to compute an
![]() $\varepsilon$
-approximation to
$\varepsilon$
-approximation to
![]() $Z_{\Lambda _n}(\lambda )$
with runtime at most
$Z_{\Lambda _n}(\lambda )$
with runtime at most
![]() $\exp\!(O(\log ^3(|\Lambda _n|/\varepsilon )))$
.
$\exp\!(O(\log ^3(|\Lambda _n|/\varepsilon )))$
.
Our second corollary applies for repulsive potentials – i.e. the case of
![]() $B = 0$
– for a much wider range of parameters. To apply Theorem 1.3 in the repulsive case, we will use pre-existing work on zero-freeness of Gibbs point process partition functions. In [Reference Michelen and Perkins19], the potential-weighted connective constant
$B = 0$
– for a much wider range of parameters. To apply Theorem 1.3 in the repulsive case, we will use pre-existing work on zero-freeness of Gibbs point process partition functions. In [Reference Michelen and Perkins19], the potential-weighted connective constant
![]() $\Delta _\phi$
was introduced, which captures a relationship between the strength of the potential and the geometry of the underlying space.
$\Delta _\phi$
was introduced, which captures a relationship between the strength of the potential and the geometry of the underlying space.
First, define
![]() $V_k$
via
$V_k$
via
 \begin{equation} V_k = \int _{(\mathbb{R}^d)^k} \prod _{j = 1}^k \!\left [ \exp \!\left ( - \sum _{i = 0}^{j - 2} \textbf{1}_{\| v_j - v_i\| \lt \|v_i - v_{i+1}\| } \phi (v_j - v_i) \right ) \cdot (1 - e^{-\phi (v_j - v_{j-1})}) \right ]\,d\textbf{v} \end{equation}
\begin{equation} V_k = \int _{(\mathbb{R}^d)^k} \prod _{j = 1}^k \!\left [ \exp \!\left ( - \sum _{i = 0}^{j - 2} \textbf{1}_{\| v_j - v_i\| \lt \|v_i - v_{i+1}\| } \phi (v_j - v_i) \right ) \cdot (1 - e^{-\phi (v_j - v_{j-1})}) \right ]\,d\textbf{v} \end{equation}
where we write
![]() $d\textbf{v} = dv_1\,dv_2\,\ldots \,d v_k$
and interpret
$d\textbf{v} = dv_1\,dv_2\,\ldots \,d v_k$
and interpret
![]() $v_0 = 0$
, and in the case of
$v_0 = 0$
, and in the case of
![]() $j = 1$
interpret the empty sum as equal to
$j = 1$
interpret the empty sum as equal to
![]() $0$
. Since the potential
$0$
. Since the potential
![]() $\phi$
is repulsive, the sequence
$\phi$
is repulsive, the sequence
![]() $\{V_k\}_{k \geqslant 1}$
is submultiplicative and so we may define the potential-weighted connective constant
$\{V_k\}_{k \geqslant 1}$
is submultiplicative and so we may define the potential-weighted connective constant
![]() $\Delta _\phi$
via
$\Delta _\phi$
via
For any repulsive potential
![]() $\phi$
we have
$\phi$
we have
![]() $\Delta _\phi \leqslant C_\phi$
where
$\Delta _\phi \leqslant C_\phi$
where
![]() $C_\phi$
is the temperedness constant defined at (1). So long as
$C_\phi$
is the temperedness constant defined at (1). So long as
![]() $\phi$
is non-trivial we in fact have
$\phi$
is non-trivial we in fact have
![]() $\Delta _\phi \lt C_\phi$
. In [Reference Michelen and Perkins19] it was shown that Assumption 1.2 is satisfied for each tempered repulsive potential for all
$\Delta _\phi \lt C_\phi$
. In [Reference Michelen and Perkins19] it was shown that Assumption 1.2 is satisfied for each tempered repulsive potential for all
![]() $\lambda _0 \lt e/\Delta _\phi$
. We, therefore, obtain the following immediate corollary.
$\lambda _0 \lt e/\Delta _\phi$
. We, therefore, obtain the following immediate corollary.
Corollary 1.5.
Let
![]() $\phi$
be a repulsive tempered potential satisfying Assumption 1.1 and let
$\phi$
be a repulsive tempered potential satisfying Assumption 1.1 and let
![]() $\Delta _\phi$
denote its potential-weighted connective constant. Let
$\Delta _\phi$
denote its potential-weighted connective constant. Let
![]() $\varepsilon \in (0,1)$
,
$\varepsilon \in (0,1)$
,
![]() $n\in \mathbb{N}$
. Then for all
$n\in \mathbb{N}$
. Then for all
![]() $\lambda \lt e/\Delta _\phi$
, there is a deterministic algorithm to compute an
$\lambda \lt e/\Delta _\phi$
, there is a deterministic algorithm to compute an
![]() $\varepsilon$
-approximation to
$\varepsilon$
-approximation to
![]() $Z_{\Lambda _n}(\lambda )$
with runtime at most
$Z_{\Lambda _n}(\lambda )$
with runtime at most
![]() $\exp\!(O(\log ^3(|\Lambda _n|/\varepsilon )))$
.
$\exp\!(O(\log ^3(|\Lambda _n|/\varepsilon )))$
.
1.3. Context and related work
Much of the classical work on Gibbs point processes has consisted of showing the absence of a phase transition when
![]() $\lambda$
is small. There are many definitions and notions of a phase transition. One of the most robust definitions is due to Lee and Yang [Reference Lee and Yang13, Reference Yang and Lee33], which states that a phase transition is a point at which the pressure fails to be analytic. Often, various other definitions of phase transitions, e.g. in terms of infinite-volume Gibbs measures, can be shown to coincide with the Lee-Yang definition (see e.g. [Reference Dobrushin and Shlosman4] for some rigorous equivalences in the discrete case).
$\lambda$
is small. There are many definitions and notions of a phase transition. One of the most robust definitions is due to Lee and Yang [Reference Lee and Yang13, Reference Yang and Lee33], which states that a phase transition is a point at which the pressure fails to be analytic. Often, various other definitions of phase transitions, e.g. in terms of infinite-volume Gibbs measures, can be shown to coincide with the Lee-Yang definition (see e.g. [Reference Dobrushin and Shlosman4] for some rigorous equivalences in the discrete case).
It remains a major open problem to demonstrate – or rule out – a phase transition for even a single non-trivial pair potential
![]() $\phi$
.Footnote
1
Groenveld [Reference Groeneveld9] used the cluster expansion to prove that no phase transition occurs for
$\phi$
.Footnote
1
Groenveld [Reference Groeneveld9] used the cluster expansion to prove that no phase transition occurs for
![]() $\lambda \lt 1/(eC_\phi )$
for repulsive potentials; this was extended to the broader class of stable potentials by Penrose [Reference Penrose24] and Ruelle [Reference Ruelle29]. For repulsive potentials, works of Meeron [Reference Meeron14, Reference Meeron15] extend this regime to
$\lambda \lt 1/(eC_\phi )$
for repulsive potentials; this was extended to the broader class of stable potentials by Penrose [Reference Penrose24] and Ruelle [Reference Ruelle29]. For repulsive potentials, works of Meeron [Reference Meeron14, Reference Meeron15] extend this regime to
![]() $1/C_\phi$
. Taking inspiration from Weitz’s groundbreaking work [Reference Weitz32] on the hard-core model – a discrete repulsive spin system – the work of the second author and Perkins [Reference Michelen and Perkins18] proved that there is no phase transition for
$1/C_\phi$
. Taking inspiration from Weitz’s groundbreaking work [Reference Weitz32] on the hard-core model – a discrete repulsive spin system – the work of the second author and Perkins [Reference Michelen and Perkins18] proved that there is no phase transition for
![]() $\lambda \lt e/C_\phi$
. This was extended further in [Reference Michelen and Perkins19], which showed that
$\lambda \lt e/C_\phi$
. This was extended further in [Reference Michelen and Perkins19], which showed that
![]() $C_\phi$
may be replaced with the potential-weighted connective constant
$C_\phi$
may be replaced with the potential-weighted connective constant
![]() $\Delta _\phi$
.
$\Delta _\phi$
.
In practice, various Markov chain Monte Carlo algorithms are used to sample from Gibbs point processes, both approximately and exactly. There is a large literature dedicated to this study, see for example [Reference Alder and Wainwright1, Reference Bernard and Krauth3, Reference Friedrich, Göbel, Krejca and Pappik7, Reference Garcia8, Reference Huber11, Reference Häggström, Van Lieshout and Møller12, Reference Møller16, Reference Møller17, Reference Michelen and Perkins20, Reference Metropolis, Rosenbluth, Rosenbluth, Teller and Teller21, Reference Preston26, Reference Propp and Wilson27]. We refer to [Reference Michelen and Perkins20] and the references therein for more context and background on these results; we also note that [Reference Michelen and Perkins20] demonstrates a fast mixing approximate sampling algorithm and polynomial-time random approximation algorithm for a repulsive Gibbs point process in the regime
![]() $\lambda \lt e/\Delta _\phi$
, the same regime in which the results of this work hold.
$\lambda \lt e/\Delta _\phi$
, the same regime in which the results of this work hold.
When it comes to deterministic algorithms, there are several results for discrete systems. In this setting, three approaches for obtaining approximation algorithms have emerged in recent years. The first is due to Weitz [Reference Weitz32] who pioneered an approach based on a notion of correlation decay (strong spatial mixing) related to the absence of phase transitions. The second is the interpolation method introduced by Barvinok [Reference Barvinok2] – a framework for showing that under a zero-freeness assumption, one can approximate the logarithm of a polynomial using a small number of Taylor coefficients (see also [Reference Patel and Regts25] for an important extension of this method). The third is a method based on the cluster expansion in statistical physics pioneered by Helmuth, Perkins, and Regts [Reference Helmuth, Perkins and Regts10] that is closely related to Barvinok’s method.
For Gibbs point processes, to our knowledge the only rigorous result giving a deterministic algorithm is that of Friedrich, Göbel, Katzmann, Krejca, and Pappik [Reference Friedrich, Göbel, Katzmann, Krejca and Pappik6]. They show that for the hard-spheres model, one may approximately compute the partition function in quasipolynomial time for
![]() $\lambda \lt e/C_\phi$
. The approach of [Reference Friedrich, Göbel, Katzmann, Krejca and Pappik6] works by showing that one may approximate the partition function of the hard-sphere model with the partition function for the hard-core model on a graph given by discretizing Euclidean space with a small mesh. After this approximation is in place, an application of Weitz’s method [Reference Weitz32] provides an algorithm. We also note that [Reference Friedrich, Göbel, Katzmann, Krejca and Pappik6] applies not only to the hard-sphere model but also to a class of multi-type Gibbs point processes with hard constraints, an example of this more general class being the Widom-Rowlinson model. Additionally, while both the algorithm of [Reference Friedrich, Göbel, Katzmann, Krejca and Pappik6] and Theorem 1.3 have quasipolynomial runtime, the algorithm of [Reference Friedrich, Göbel, Katzmann, Krejca and Pappik6] runs in time
$\lambda \lt e/C_\phi$
. The approach of [Reference Friedrich, Göbel, Katzmann, Krejca and Pappik6] works by showing that one may approximate the partition function of the hard-sphere model with the partition function for the hard-core model on a graph given by discretizing Euclidean space with a small mesh. After this approximation is in place, an application of Weitz’s method [Reference Weitz32] provides an algorithm. We also note that [Reference Friedrich, Göbel, Katzmann, Krejca and Pappik6] applies not only to the hard-sphere model but also to a class of multi-type Gibbs point processes with hard constraints, an example of this more general class being the Widom-Rowlinson model. Additionally, while both the algorithm of [Reference Friedrich, Göbel, Katzmann, Krejca and Pappik6] and Theorem 1.3 have quasipolynomial runtime, the algorithm of [Reference Friedrich, Göbel, Katzmann, Krejca and Pappik6] runs in time
![]() $\exp\!(O( \log ^2 (|\Lambda _n|/\varepsilon ))$
rather than our runtime of
$\exp\!(O( \log ^2 (|\Lambda _n|/\varepsilon ))$
rather than our runtime of
![]() $\exp\!(O( \log ^3 (|\Lambda _n|/\varepsilon )).$
$\exp\!(O( \log ^3 (|\Lambda _n|/\varepsilon )).$
To our knowledge, Theorem 1.3 marks the first approximation algorithm of any kind for the partition function for stable, non-repulsive potentials.
1.4. Our approach
Our approach is via Barvinok’s interpolation method combined with use of the cluster expansion. The cluster expansion – also called the Meyer series – is a combinatorial description of the Taylor coefficients of
![]() $\log Z_S(\lambda )$
. In particular for bounded, measurable
$\log Z_S(\lambda )$
. In particular for bounded, measurable
![]() $S\subset \mathbb{R}^d$
and
$S\subset \mathbb{R}^d$
and
![]() $|\lambda | \lt (e^{1+B} \hat C_\phi )^{-1}$
, we have
$|\lambda | \lt (e^{1+B} \hat C_\phi )^{-1}$
, we have
 \begin{align} \log Z_S(\lambda ) = \sum _{k \geqslant 1} \frac{\lambda ^k}{k!} C_k(S) \end{align}
\begin{align} \log Z_S(\lambda ) = \sum _{k \geqslant 1} \frac{\lambda ^k}{k!} C_k(S) \end{align}
where
![]() $\mathcal{G}_k$
is the set of connected labelled graphs with
$\mathcal{G}_k$
is the set of connected labelled graphs with
![]() $k$
vertices and
$k$
vertices and
![]() $E(G)$
is the set of edges in a graph
$E(G)$
is the set of edges in a graph
![]() $G$
(see, e.g., [Reference Procacci and Yuhjtman28] for this and similar expansions).
$G$
(see, e.g., [Reference Procacci and Yuhjtman28] for this and similar expansions).
The algorithmic significance of the cluster expansion stems from two observations. The first is that in order to compute
![]() $\frac{1}{|S|}\log Z_S(\lambda )$
up to an additive error of
$\frac{1}{|S|}\log Z_S(\lambda )$
up to an additive error of
![]() $\varepsilon$
, it suffices to compute the first
$\varepsilon$
, it suffices to compute the first
![]() $O(\log\!(|S|/\varepsilon ))$
coefficients
$O(\log\!(|S|/\varepsilon ))$
coefficients
![]() $C_k(S)$
. This simple but crucial observation is at the heart of Barvinok’s interpolation method and algorithmic applications of the cluster expansion. The second is that the description of the Taylor coefficients as a sum over connected graphs allows us to approximate them efficiently.
$C_k(S)$
. This simple but crucial observation is at the heart of Barvinok’s interpolation method and algorithmic applications of the cluster expansion. The second is that the description of the Taylor coefficients as a sum over connected graphs allows us to approximate them efficiently.
At first sight, it seems that the use of the cluster expansion restricts the range of
![]() $\lambda$
for which we can obtain algorithms to the interval
$\lambda$
for which we can obtain algorithms to the interval
![]() $(0, ( e^{1+B} \hat C_\phi )^{-1})$
where the cluster expansion is known to converge. Moreover, the work of Groeneveld [Reference Groeneveld9] and Penrose [Reference Penrose24] implies that for a repulsive potential, the radius of convergence of the cluster expansion is at most
$(0, ( e^{1+B} \hat C_\phi )^{-1})$
where the cluster expansion is known to converge. Moreover, the work of Groeneveld [Reference Groeneveld9] and Penrose [Reference Penrose24] implies that for a repulsive potential, the radius of convergence of the cluster expansion is at most
![]() $1/C_\phi$
(see Remark 3.7 in [Reference Nguyen and Fernández23]). In order to use the cluster expansion to produce an algorithm throughout the zero-free region (which for repulsive potentials is known to include values of
$1/C_\phi$
(see Remark 3.7 in [Reference Nguyen and Fernández23]). In order to use the cluster expansion to produce an algorithm throughout the zero-free region (which for repulsive potentials is known to include values of
![]() $\lambda$
outside of the radius of convergence), we use an idea of Barvinok and apply a well-chosen polynomial to map between the zero-free region and the disk. This is handled in Section 3.
$\lambda$
outside of the radius of convergence), we use an idea of Barvinok and apply a well-chosen polynomial to map between the zero-free region and the disk. This is handled in Section 3.
The main technical contribution of this work is to approximate the coefficients of the cluster expansion (11) in quasipolynomial time. We note that the problem of approximating coefficients of the cluster expansion was pointed out in [Reference Friedrich, Göbel, Katzmann, Krejca and Pappik6] as a central obstacle to obtaining an efficient deterministic algorithm that works entirely in the continuum. To approximate the coefficients
![]() $C_k(S)$
, the main challenge is that for each graph
$C_k(S)$
, the main challenge is that for each graph
![]() $G \in \mathcal{G}_k$
, the integrand in (11) need not be well-behaved; in particular, it need not be Lipschitz. To handle this, we break each such term into many subsequent terms, each of which will give us an integral of a function that is Lipschitz over its support. We then approximate each of these integrals by taking a sufficiently fine mesh and comparing the integral to a weighted sum over this mesh. Our assumption that the potential
$G \in \mathcal{G}_k$
, the integrand in (11) need not be well-behaved; in particular, it need not be Lipschitz. To handle this, we break each such term into many subsequent terms, each of which will give us an integral of a function that is Lipschitz over its support. We then approximate each of these integrals by taking a sufficiently fine mesh and comparing the integral to a weighted sum over this mesh. Our assumption that the potential
![]() $\phi$
has finite range allows us to restrict our attention to approximating integrals over regions whose volume is independent of
$\phi$
has finite range allows us to restrict our attention to approximating integrals over regions whose volume is independent of
![]() $n$
. It would be interesting to extend the results of this paper to include stable potentials of infinite range.
$n$
. It would be interesting to extend the results of this paper to include stable potentials of infinite range.
2. Approximating coefficients in the cluster expansion
Throughout this section, we fix a stable potential
![]() $\phi$
with stability constant
$\phi$
with stability constant
![]() $B$
that satisfies Assumption 1.1. Recall that
$B$
that satisfies Assumption 1.1. Recall that
![]() $\Lambda _n\;:\!=\; [\!-\!n,n]^d \subset \mathbb{R}^d$
. Our goal in this section is to provide an approximation algorithm for
$\Lambda _n\;:\!=\; [\!-\!n,n]^d \subset \mathbb{R}^d$
. Our goal in this section is to provide an approximation algorithm for
![]() $C_k(\Lambda _n)$
(as defined at (11)). In the next section, we show how to use these approximate coefficients to arrive at an approximation of the partition function
$C_k(\Lambda _n)$
(as defined at (11)). In the next section, we show how to use these approximate coefficients to arrive at an approximation of the partition function
![]() $Z_{\Lambda _n}(\lambda )$
.
$Z_{\Lambda _n}(\lambda )$
.
Proposition 2.1.
Let
![]() $\phi$
be a stable potential satisfying Assumption 1.1. There are constants
$\phi$
be a stable potential satisfying Assumption 1.1. There are constants
![]() $C, c \gt 0$
depending only on
$C, c \gt 0$
depending only on
![]() $\phi$
and the dimension
$\phi$
and the dimension
![]() $d$
so that the following holds. For each
$d$
so that the following holds. For each
![]() $\varepsilon \in (0,1)$
and
$\varepsilon \in (0,1)$
and
![]() $k,n \in \mathbb{N}$
, we may approximate
$k,n \in \mathbb{N}$
, we may approximate
![]() $C_k(\Lambda _n)/|\Lambda _n|$
up to an additive error of
$C_k(\Lambda _n)/|\Lambda _n|$
up to an additive error of
![]() $\varepsilon$
in time at most
$\varepsilon$
in time at most
![]() $C |\Lambda _n| \varepsilon ^{-dk} e^{ck^3}$
.
$C |\Lambda _n| \varepsilon ^{-dk} e^{ck^3}$
.
Note that Proposition 2.1 makes no use of a zero-freeness or correlation decay type assumption.
In order to prove Proposition 2.1, we will approximate each summand in (11). Further, we will break up the term for each graph into the terms that are Lipschitz on their support. The main work of this section is Lemma 2.3 below, which provides an approximation for each of these Lipschitz terms. Before stating this precisely, we make a few definitions.
Definition 2.2. Let
![]() $\Delta _1,\ldots, \Delta _\ell$
be defined as in Assumption 1.1.
$\Delta _1,\ldots, \Delta _\ell$
be defined as in Assumption 1.1.
-
1. Given a connected graph
 $G$
on
$G$
on
 $k$
vertices, an edge-labelling is a function
$k$
vertices, an edge-labelling is a function
 $\sigma \;:\;E(G) \to{= \{1, \ldots, l\}}$
.
$\sigma \;:\;E(G) \to{= \{1, \ldots, l\}}$
. -
2. For each labelling,
 $\sigma$
and edge
$\sigma$
and edge
 $\{i,j\} \in E(G)$
define the function
$\{i,j\} \in E(G)$
define the function
 $f_{i,j}^\sigma \;:\;(\mathbb{R}^d)^k \to{\mathbb R}$
via
$f_{i,j}^\sigma \;:\;(\mathbb{R}^d)^k \to{\mathbb R}$
via \begin{equation*}f_{i,j}^{\sigma }(\textbf{x}) \;:\!=\; (e^{-\phi (x_i - x_j)} - 1) \textbf{1}\{ x_i - x_j \in \Delta _{\sigma (\{i,j\})} \}.\end{equation*}
\begin{equation*}f_{i,j}^{\sigma }(\textbf{x}) \;:\!=\; (e^{-\phi (x_i - x_j)} - 1) \textbf{1}\{ x_i - x_j \in \Delta _{\sigma (\{i,j\})} \}.\end{equation*}
-
3. Define
 $f^{\sigma }$
via
$f^{\sigma }$
via \begin{equation*} f^{\sigma }(\textbf{x}) \;:\!=\; \prod _{\{i,j\} \in E(G)} f_{i,j}^{\sigma }(\textbf{x})\, .\end{equation*}
\begin{equation*} f^{\sigma }(\textbf{x}) \;:\!=\; \prod _{\{i,j\} \in E(G)} f_{i,j}^{\sigma }(\textbf{x})\, .\end{equation*}
-
4. Define
 $A_\sigma \subset (\mathbb{R}^d)^k$
viaand note that
$A_\sigma \subset (\mathbb{R}^d)^k$
viaand note that \begin{equation*} A_\sigma \;:\!=\; \{\textbf{x} \in (\mathbb {R}^d)^k \;:\;x_i - x_j \in \Delta _{\sigma (\{i,j\}) }\text { for all }\{i,j\} \in E(G) \}, \end{equation*}
\begin{equation*} A_\sigma \;:\!=\; \{\textbf{x} \in (\mathbb {R}^d)^k \;:\;x_i - x_j \in \Delta _{\sigma (\{i,j\}) }\text { for all }\{i,j\} \in E(G) \}, \end{equation*}
 $\mathrm{supp}(f^\sigma ) \subseteq A_\sigma$
.
$\mathrm{supp}(f^\sigma ) \subseteq A_\sigma$
.
Recall that
![]() $\mathcal{G}_k$
is the set of connected labelled graphs with
$\mathcal{G}_k$
is the set of connected labelled graphs with
![]() $k$
vertices. Given a graph
$k$
vertices. Given a graph
![]() $G \in \mathcal{G}_k$
we have
$G \in \mathcal{G}_k$
we have
where the sum ranges over all edge-labellings
![]() $\sigma$
of
$\sigma$
of
![]() $G$
. We note that there are
$G$
. We note that there are
![]() $\ell ^{|E(G)|} \leqslant \ell ^{k^2/2}$
such labellings, and there are at most
$\ell ^{|E(G)|} \leqslant \ell ^{k^2/2}$
such labellings, and there are at most
![]() $2^{k^2/2}$
connected graphs on
$2^{k^2/2}$
connected graphs on
![]() $k$
vertices.
$k$
vertices.
With this setup in mind, in order to approximate
![]() $C_k(\Lambda _n)$
, it is sufficient to approximate the integral of
$C_k(\Lambda _n)$
, it is sufficient to approximate the integral of
![]() $f^\sigma$
for each labelling
$f^\sigma$
for each labelling
![]() $\sigma$
of each graph
$\sigma$
of each graph
![]() $G \in \mathcal{G}_k$
. In the next subsection, we will demonstrate such an approximation:
$G \in \mathcal{G}_k$
. In the next subsection, we will demonstrate such an approximation:
Lemma 2.3.
Let
![]() $n,k\in \mathbb{N}$
. For any
$n,k\in \mathbb{N}$
. For any
![]() $G \in \mathcal{G}_k$
, labelling
$G \in \mathcal{G}_k$
, labelling
![]() $\sigma$
, and
$\sigma$
, and
![]() $\delta \lt c_{d,R}$
, there is a set of points
$\delta \lt c_{d,R}$
, there is a set of points
![]() $\mathcal{S}_{\sigma,\delta } \subset \Lambda _n^k$
with
$\mathcal{S}_{\sigma,\delta } \subset \Lambda _n^k$
with
![]() $|\mathcal{S}_{\sigma,\delta }| = O(|\Lambda _n|(2R)^{d(k-1)}\delta ^{-dk} )$
so that we have
$|\mathcal{S}_{\sigma,\delta }| = O(|\Lambda _n|(2R)^{d(k-1)}\delta ^{-dk} )$
so that we have
 \begin{equation*}\left |\int _{\Lambda _n^k} f^\sigma (\textbf{{x}}) \,d\textbf{{x}} - \sum _{\textbf{{x}} \in \mathcal {S}_{\sigma,\delta }} \delta ^{dk} f^\sigma (\textbf{{x}}) \right | = O(k^2{e^{Bk^2}} \delta |\Lambda _n| (2R)^{d(k-1)} ). \end{equation*}
\begin{equation*}\left |\int _{\Lambda _n^k} f^\sigma (\textbf{{x}}) \,d\textbf{{x}} - \sum _{\textbf{{x}} \in \mathcal {S}_{\sigma,\delta }} \delta ^{dk} f^\sigma (\textbf{{x}}) \right | = O(k^2{e^{Bk^2}} \delta |\Lambda _n| (2R)^{d(k-1)} ). \end{equation*}
Further, the set
![]() $\mathcal{S}_{\sigma,\delta }$
may be computed in time
$\mathcal{S}_{\sigma,\delta }$
may be computed in time
![]() $O(k^2|\Lambda _n|(2R)^{d(k-1)}\delta ^{-dk} )$
.
$O(k^2|\Lambda _n|(2R)^{d(k-1)}\delta ^{-dk} )$
.
Proposition 2.1 follows quickly from here.
Proof of Proposition 2.1. Note that by (12)
Taking
![]() $\delta = \varepsilon \exp\!(\!-\!Ck^2)$
in Lemma 2.3 with
$\delta = \varepsilon \exp\!(\!-\!Ck^2)$
in Lemma 2.3 with
![]() $C$
sufficiently large as a function of
$C$
sufficiently large as a function of
![]() $R,d,\ell$
and
$R,d,\ell$
and
![]() $B$
we may approximate
$B$
we may approximate
![]() $C_k(\Lambda _n)/|\Lambda _n|$
up to additive error
$C_k(\Lambda _n)/|\Lambda _n|$
up to additive error
![]() $\varepsilon$
in time
$\varepsilon$
in time
![]() $O(k^2{e^{Bk^2}}|\Lambda _n| (2R)^{d(k-1)}\delta ^{-dk} )= O(|\Lambda _n| \varepsilon ^{-dk} e^{ck^3})$
where
$O(k^2{e^{Bk^2}}|\Lambda _n| (2R)^{d(k-1)}\delta ^{-dk} )= O(|\Lambda _n| \varepsilon ^{-dk} e^{ck^3})$
where
![]() $c$
is a constant depending only on
$c$
is a constant depending only on
![]() $R,d$
and
$R,d$
and
![]() $\ell$
and
$\ell$
and
![]() $B$
.
$B$
.
2.1. Approximating the integral over a labelling
In this section, we prove Lemma 2.3. Fix
![]() $G\in \mathcal{G}_k$
and set
$G\in \mathcal{G}_k$
and set
![]() $S = \Lambda _n$
.
$S = \Lambda _n$
.
Recall from Assumption 1.1 that the sets
![]() $\Delta _j$
are defined via
$\Delta _j$
are defined via
![]() $\Delta _j = K_j \setminus K_{j - 1}$
. For a given
$\Delta _j = K_j \setminus K_{j - 1}$
. For a given
![]() $\gamma \geqslant 0$
,
$\gamma \geqslant 0$
,
Define the set
![]() $U_\gamma$
via
$U_\gamma$
via
Before continuing, let us motivate the definition of
![]() $U_\gamma$
. We will show that if
$U_\gamma$
. We will show that if
![]() $\textbf{x}\in U_\gamma$
, then
$\textbf{x}\in U_\gamma$
, then
![]() $f^\sigma$
is Lipschitz on a small neighbourhood of
$f^\sigma$
is Lipschitz on a small neighbourhood of
![]() $\textbf{x}$
(see Lemmas 2.8 and 2.7 below). This will allow us to approximate the integral
$\textbf{x}$
(see Lemmas 2.8 and 2.7 below). This will allow us to approximate the integral
![]() $\int _{U_\gamma } f^\sigma (\textbf{x})\,d\textbf{x}$
by a sum over a mesh. Indeed, we define
$\int _{U_\gamma } f^\sigma (\textbf{x})\,d\textbf{x}$
by a sum over a mesh. Indeed, we define
and prove the following lemma.
Lemma 2.4.
 \begin{equation*}\left |\int _{U_\gamma } f^\sigma (\textbf{{x}})\,d\textbf{{x}} - \sum _{\textbf{{x}} \in \mathcal {S}_{\sigma,\delta }} \delta ^{dk} f^\sigma (\textbf{{x}})\right | = O(k^2 {e^{Bk^2}}\delta |S| (2R)^{d(k-1)} ). \end{equation*}
\begin{equation*}\left |\int _{U_\gamma } f^\sigma (\textbf{{x}})\,d\textbf{{x}} - \sum _{\textbf{{x}} \in \mathcal {S}_{\sigma,\delta }} \delta ^{dk} f^\sigma (\textbf{{x}})\right | = O(k^2 {e^{Bk^2}}\delta |S| (2R)^{d(k-1)} ). \end{equation*}
To complete the proof of Lemma 2.3 we show that
![]() $\int _{U_\gamma } f^\sigma (\textbf{x})\,d\textbf{x}$
closely approximates
$\int _{U_\gamma } f^\sigma (\textbf{x})\,d\textbf{x}$
closely approximates
![]() $\int _{\Lambda _n^k} f^\sigma (\textbf{x}) \,d\textbf{x}$
and that the sum in Lemma 2.4 can be computed efficiently. We turn our attention first to the latter task.
$\int _{\Lambda _n^k} f^\sigma (\textbf{x}) \,d\textbf{x}$
and that the sum in Lemma 2.4 can be computed efficiently. We turn our attention first to the latter task.
Lemma 2.5.
The set
![]() $\mathcal{S}_{\sigma,\delta }$
may be enumerated in time
$\mathcal{S}_{\sigma,\delta }$
may be enumerated in time
![]() $O(k^2|S| (2R)^{d(k-1)}) \delta ^{-dk})$
and satisfies
$O(k^2|S| (2R)^{d(k-1)}) \delta ^{-dk})$
and satisfies
![]() $|\mathcal{S}_{\sigma,\delta }| = O(|S| (2R)^{d(k-1)}) \delta ^{-dk})$
.
$|\mathcal{S}_{\sigma,\delta }| = O(|S| (2R)^{d(k-1)}) \delta ^{-dk})$
.
Proof. Fix a spanning tree
![]() $T$
of
$T$
of
![]() $G$
and let
$G$
and let
First observe that
![]() $\mathcal{S}_{\sigma,\delta }\subseteq \mathcal{T}$
, since if
$\mathcal{S}_{\sigma,\delta }\subseteq \mathcal{T}$
, since if
![]() $\textbf{x}\in U_\gamma$
then
$\textbf{x}\in U_\gamma$
then
![]() $x_i-x_j\in \Delta ^{(\gamma )}_{\sigma (\{i,j\})}\subseteq [\!-\!R,R]^d$
for all
$x_i-x_j\in \Delta ^{(\gamma )}_{\sigma (\{i,j\})}\subseteq [\!-\!R,R]^d$
for all
![]() $ \{i,j\} \in E(G)$
. In particular,
$ \{i,j\} \in E(G)$
. In particular,
![]() $\|x_i - x_j\|_\infty \leqslant 2R$
for all
$\|x_i - x_j\|_\infty \leqslant 2R$
for all
![]() $ \{i,j\} \in E(T)$
.
$ \{i,j\} \in E(T)$
.
Note that
![]() $|\mathcal{T}| = O(|S|(2R)^{d(k-1)}\delta ^{-dk} )$
and that
$|\mathcal{T}| = O(|S|(2R)^{d(k-1)}\delta ^{-dk} )$
and that
![]() $\mathcal{T}$
may be enumerated in time
$\mathcal{T}$
may be enumerated in time
![]() $O(|S|(2R)^{d(k-1)}\delta ^{-dk} )$
as well. Further, for each point in
$O(|S|(2R)^{d(k-1)}\delta ^{-dk} )$
as well. Further, for each point in
![]() $\mathcal{T}$
, we may check membership in
$\mathcal{T}$
, we may check membership in
![]() $\mathcal{S}_{\sigma,\delta }$
in time
$\mathcal{S}_{\sigma,\delta }$
in time
![]() $O(k^2)$
, completing the lemma.
$O(k^2)$
, completing the lemma.
To show that
![]() $\int _{U_\gamma } f^\sigma (\textbf{x})\,d\textbf{x}$
closely approximates
$\int _{U_\gamma } f^\sigma (\textbf{x})\,d\textbf{x}$
closely approximates
![]() $\int _{S^k} f^\sigma (\textbf{x}) \,d\textbf{x}$
it will be enough to show that the measure of
$\int _{S^k} f^\sigma (\textbf{x}) \,d\textbf{x}$
it will be enough to show that the measure of
is small.
Lemma 2.6.
For
![]() $\gamma \leqslant 1/d$
, we have
$\gamma \leqslant 1/d$
, we have
![]() $|W_\gamma | \leqslant 4|S| |E(G)| (2R)^{d(k-1)} d \gamma$
.
$|W_\gamma | \leqslant 4|S| |E(G)| (2R)^{d(k-1)} d \gamma$
.
Proof. For each edge,
![]() $\{a,b\} \in E(G)$
define
$\{a,b\} \in E(G)$
define
Note then that
![]() $W_\gamma \subseteq \cup _{\{a,b\}\in E(G) } W_{\gamma,a,b}$
. Thus, it is sufficient to prove
$W_\gamma \subseteq \cup _{\{a,b\}\in E(G) } W_{\gamma,a,b}$
. Thus, it is sufficient to prove
To see (13), fix a spanning tree
![]() $T$
of
$T$
of
![]() $G$
so that
$G$
so that
![]() $\{a,b\} \in E(T)$
. We then have that
$\{a,b\} \in E(T)$
. We then have that
This provides a bound of
Write
![]() $j = \sigma (\{a,b\})$
for notational simplicity. By convexity of the sets
$j = \sigma (\{a,b\})$
for notational simplicity. By convexity of the sets
![]() $K_j$
and
$K_j$
and
![]() $K_{j-1}$
we have
$K_{j-1}$
we have
![]() $(1-\gamma )K_j\subset K_j$
and
$(1-\gamma )K_j\subset K_j$
and
![]() $K_{j-1}\subset (1+\gamma )K_{j-1}$
. We may therefore bound
$K_{j-1}\subset (1+\gamma )K_{j-1}$
. We may therefore bound
 \begin{align} | \Delta _{j} \setminus \Delta _{j}^{(\gamma )}| &\leqslant |K_j| - |(1-\gamma )K_j| + |(1 + \gamma )K_{j-1}| - |K_{j-1}| \nonumber \\[5pt] &= |K_j| \left (1 - (1 - \gamma )^d \right ) + |K_{j-1}|\left ((1 + \gamma )^d - 1\right ) \nonumber \\[5pt] &\leqslant (2R)^d \cdot 2d\gamma + (2R)^d \cdot 2d\gamma . \end{align}
\begin{align} | \Delta _{j} \setminus \Delta _{j}^{(\gamma )}| &\leqslant |K_j| - |(1-\gamma )K_j| + |(1 + \gamma )K_{j-1}| - |K_{j-1}| \nonumber \\[5pt] &= |K_j| \left (1 - (1 - \gamma )^d \right ) + |K_{j-1}|\left ((1 + \gamma )^d - 1\right ) \nonumber \\[5pt] &\leqslant (2R)^d \cdot 2d\gamma + (2R)^d \cdot 2d\gamma . \end{align}
Combining the two previously displayed equations shows (13) and completes the lemma.
Assuming Lemma 2.4, the proof of Lemma 2.3 now follows quickly.
Proof of Lemma 2.3. Bound
 \begin{align} \left |\int _{S^k} f^\sigma (\textbf{x}) \,d\textbf{x} - \sum _{\textbf{x} \in \mathcal{S}_{\sigma,\delta }} \delta ^{dk} f^\sigma (\textbf{x}) \right | &\leqslant \!\left |\int _{S^k \setminus U_\gamma } f^\sigma (\textbf{x}) \,d\textbf{x}\right | + \left |\int _{U_\gamma } f^\sigma (\textbf{x})\,d\textbf{x} - \sum _{\textbf{x} \in \mathcal{S}_{\sigma,\delta }} \delta ^{dk} f^\sigma (\textbf{x})\right |. \end{align}
\begin{align} \left |\int _{S^k} f^\sigma (\textbf{x}) \,d\textbf{x} - \sum _{\textbf{x} \in \mathcal{S}_{\sigma,\delta }} \delta ^{dk} f^\sigma (\textbf{x}) \right | &\leqslant \!\left |\int _{S^k \setminus U_\gamma } f^\sigma (\textbf{x}) \,d\textbf{x}\right | + \left |\int _{U_\gamma } f^\sigma (\textbf{x})\,d\textbf{x} - \sum _{\textbf{x} \in \mathcal{S}_{\sigma,\delta }} \delta ^{dk} f^\sigma (\textbf{x})\right |. \end{align}
Since
![]() $|e^{-\phi (x)} - 1| \leqslant e^{2B}$
, we have that
$|e^{-\phi (x)} - 1| \leqslant e^{2B}$
, we have that
![]() $|f^\sigma | \leqslant e^{Bk^2 }$
. The first term on the RHS of (15) may thus be bounded by
$|f^\sigma | \leqslant e^{Bk^2 }$
. The first term on the RHS of (15) may thus be bounded by
![]() ${e^{Bk^2 }}|W_\gamma |$
, which we bound using Lemma 2.6, and the latter term may be bounded by Lemma 2.4.
${e^{Bk^2 }}|W_\gamma |$
, which we bound using Lemma 2.6, and the latter term may be bounded by Lemma 2.4.
It remains to prove Lemma 2.4. As discussed, a key step will be to show that if
![]() $\textbf{x}\in U_\gamma$
, then
$\textbf{x}\in U_\gamma$
, then
![]() $f^\sigma$
is Lipschitz on a small neighbourhood of
$f^\sigma$
is Lipschitz on a small neighbourhood of
![]() $\textbf{x}$
. This is carried out in the following two lemmas.
$\textbf{x}$
. This is carried out in the following two lemmas.
Lemma 2.7.
The function
![]() $f^{\sigma }$
is
$f^{\sigma }$
is
![]() $(2{e^{Bk^2}} L|E(G)|)$
-Lipschitz on
$(2{e^{Bk^2}} L|E(G)|)$
-Lipschitz on
![]() $A_\sigma$
.
$A_\sigma$
.
Proof. Let
![]() $\textbf{x}, \textbf{y} \in A_\sigma$
. Then by definition
$\textbf{x}, \textbf{y} \in A_\sigma$
. Then by definition
 \begin{align} |f^{\sigma }(\textbf{x})-f^{\sigma }(\textbf{y})|= \left |\prod _{\{i,j\} \in E(G)} (e^{-\phi (x_i - x_j)} - 1) - \prod _{\{i,j\} \in E(G)} (e^{-\phi (y_i - y_j)} - 1) \right |\, . \end{align}
\begin{align} |f^{\sigma }(\textbf{x})-f^{\sigma }(\textbf{y})|= \left |\prod _{\{i,j\} \in E(G)} (e^{-\phi (x_i - x_j)} - 1) - \prod _{\{i,j\} \in E(G)} (e^{-\phi (y_i - y_j)} - 1) \right |\, . \end{align}
To bound (16) we use the inequality
 \begin{equation*} \left |\prod _{i=1}^mz_i - \prod _{i=1}^mw_i\right |\leqslant {T^{m-1}}\sum _{i=1}^m|z_i-w_i|, \end{equation*}
\begin{equation*} \left |\prod _{i=1}^mz_i - \prod _{i=1}^mw_i\right |\leqslant {T^{m-1}}\sum _{i=1}^m|z_i-w_i|, \end{equation*}
which holds whenever
![]() $|z_i|\leqslant{T}, |w_i|\leqslant{T}$
for all
$|z_i|\leqslant{T}, |w_i|\leqslant{T}$
for all
![]() $i$
. This yields
$i$
. This yields
 \begin{align*} |f^{\sigma }(\textbf{x})-f^{\sigma }(\textbf{y})| &\leqslant{e^{B k^2}} \sum _{\{i,j\} \in E(G)} \!\left | e^{-\phi (x_i - x_j)} - e^{-\phi (y_i - y_j)} \right | \\[5pt] & \leqslant{e^{B k^2}} |E(G)| L \max _{\{i,j\} \in E(G)} \|(x_i-y_i) -(x_j-y_j) \|_2 \\[5pt] &\leqslant 2{e^{Bk^2}} |E(G)|L \|\textbf{x}-\textbf{y}\|_2, \end{align*}
\begin{align*} |f^{\sigma }(\textbf{x})-f^{\sigma }(\textbf{y})| &\leqslant{e^{B k^2}} \sum _{\{i,j\} \in E(G)} \!\left | e^{-\phi (x_i - x_j)} - e^{-\phi (y_i - y_j)} \right | \\[5pt] & \leqslant{e^{B k^2}} |E(G)| L \max _{\{i,j\} \in E(G)} \|(x_i-y_i) -(x_j-y_j) \|_2 \\[5pt] &\leqslant 2{e^{Bk^2}} |E(G)|L \|\textbf{x}-\textbf{y}\|_2, \end{align*}
where we used that
![]() $x\mapsto \exp\!(\!-\!\phi (x))$
is
$x\mapsto \exp\!(\!-\!\phi (x))$
is
![]() $L$
-Lipschitz on each
$L$
-Lipschitz on each
![]() $\Delta _j$
by Assumption 1.1.
$\Delta _j$
by Assumption 1.1.
Set
Since we are working in the context of Lemma 2.3, we may also assume that
![]() $\gamma \leqslant 1/d$
by taking
$\gamma \leqslant 1/d$
by taking
![]() $\delta$
small enough as a function of
$\delta$
small enough as a function of
![]() $d$
and
$d$
and
![]() $R$
.
$R$
.
Lemma 2.8.
Let
![]() $\gamma$
be as in (17). If
$\gamma$
be as in (17). If
![]() $\textbf{{x}}\in U_\gamma$
, then
$\textbf{{x}}\in U_\gamma$
, then
where
![]() $B_\infty (\textbf{{x}};\; \delta )$
denotes the open
$B_\infty (\textbf{{x}};\; \delta )$
denotes the open
![]() $\ell _\infty$
ball of radius
$\ell _\infty$
ball of radius
![]() $\delta$
centred at
$\delta$
centred at
![]() $\textbf{{x}}$
.
$\textbf{{x}}$
.
Proof. Let
![]() $\textbf{x}\in U_\gamma \subseteq \mathrm{supp}(f^{\sigma })$
. Suppose that
$\textbf{x}\in U_\gamma \subseteq \mathrm{supp}(f^{\sigma })$
. Suppose that
![]() $\textbf{v}\in (\mathbb{R}^d)^k$
is such that
$\textbf{v}\in (\mathbb{R}^d)^k$
is such that
![]() $\|\textbf{v}\|_\infty \lt \delta$
. It suffices to show that
$\|\textbf{v}\|_\infty \lt \delta$
. It suffices to show that
![]() $\textbf{x}+\textbf{v}\in A_{\sigma }$
. Let
$\textbf{x}+\textbf{v}\in A_{\sigma }$
. Let
![]() $\{i,j\}\in E(G)$
and let
$\{i,j\}\in E(G)$
and let
![]() $t=\sigma (\{i,j\})$
. Our task is to verify that
$t=\sigma (\{i,j\})$
. Our task is to verify that
Since
![]() $\textbf{x}\in U_\gamma$
we have, by definition,
$\textbf{x}\in U_\gamma$
we have, by definition,
Moreover
![]() $\|v_i - v_j\|_\infty \leqslant 2\delta$
. The statement (18) then follows from the following claim.
$\|v_i - v_j\|_\infty \leqslant 2\delta$
. The statement (18) then follows from the following claim.
Claim 2.9.
If
![]() $\textbf{y}\in \Delta ^{(\gamma )}_{t}$
, then
$\textbf{y}\in \Delta ^{(\gamma )}_{t}$
, then
![]() $B_\infty (\textbf{y};\; 2\delta )\subseteq \Delta _{t}.$
$B_\infty (\textbf{y};\; 2\delta )\subseteq \Delta _{t}.$
Proof. Recall that
We will show that
![]() $B_\infty (\textbf{y};\; 2\delta )\subseteq K_t$
. The argument to show that
$B_\infty (\textbf{y};\; 2\delta )\subseteq K_t$
. The argument to show that
![]() $B_\infty (\textbf{y};\; 2\delta )\subseteq K_{t-1}^c$
is analogous. We let
$B_\infty (\textbf{y};\; 2\delta )\subseteq K_{t-1}^c$
is analogous. We let
![]() $\|\cdot \|$
denote the norm associated to the centrally symmetric convex set
$\|\cdot \|$
denote the norm associated to the centrally symmetric convex set
![]() $K_t$
, that is for
$K_t$
, that is for
![]() $\textbf{u} \in \mathbb{R}^{d}$
,
$\textbf{u} \in \mathbb{R}^{d}$
,
We note that since
![]() $[\!-\!1/R,1/R]^d\subseteq K_t \subseteq [R,R]^d$
by assumption, we have
$[\!-\!1/R,1/R]^d\subseteq K_t \subseteq [R,R]^d$
by assumption, we have
With these observations in hand, we note that since
![]() $\textbf{y} \in \Delta ^{(\gamma )}_{t}\subseteq (1-\gamma )K_t$
, we have
$\textbf{y} \in \Delta ^{(\gamma )}_{t}\subseteq (1-\gamma )K_t$
, we have
![]() $\|\textbf{y}\|\leqslant (1-\gamma )$
. Suppose now that
$\|\textbf{y}\|\leqslant (1-\gamma )$
. Suppose now that
![]() $\|\textbf{z}\|_\infty \lt 2\delta$
, then by the triangle inequality, (17) and (19)
$\|\textbf{z}\|_\infty \lt 2\delta$
, then by the triangle inequality, (17) and (19)
In other words
![]() $\textbf{y} +\textbf{z}\in K_t$
as desired.
$\textbf{y} +\textbf{z}\in K_t$
as desired.
With the previous two lemmas in hand, we are now in a position to prove Lemma 2.4.
Proof of Lemma
2.4. Given
![]() $\textbf{x}\in (\mathbb{R}^{d})^k$
, let
$\textbf{x}\in (\mathbb{R}^{d})^k$
, let
![]() $r(\textbf{x})$
denote the point in
$r(\textbf{x})$
denote the point in
![]() $((\delta \mathbb{Z})^d)^k$
closest to
$((\delta \mathbb{Z})^d)^k$
closest to
![]() $\textbf{x}$
in
$\textbf{x}$
in
![]() $\ell _\infty$
distance (breaking ties arbitrarily). Note that if
$\ell _\infty$
distance (breaking ties arbitrarily). Note that if
![]() $\textbf{x}\in U_\gamma$
then
$\textbf{x}\in U_\gamma$
then
![]() $r(\textbf{x})\in A_\sigma$
by Lemma 2.8. It follows from Lemma 2.7 that
$r(\textbf{x})\in A_\sigma$
by Lemma 2.8. It follows from Lemma 2.7 that
 \begin{align} \left |\int _{U_\gamma } f^\sigma (\textbf{x}) - f^\sigma (r(\textbf{x}))\,d\textbf{x}\right | \leqslant 2{e^{Bk^2}}LE(G)\sqrt{dk}\delta |U_\gamma |= O({e^{Bk^2}}|E(G)|\delta |S| (2R)^{d(k-1)} ) \, . \end{align}
\begin{align} \left |\int _{U_\gamma } f^\sigma (\textbf{x}) - f^\sigma (r(\textbf{x}))\,d\textbf{x}\right | \leqslant 2{e^{Bk^2}}LE(G)\sqrt{dk}\delta |U_\gamma |= O({e^{Bk^2}}|E(G)|\delta |S| (2R)^{d(k-1)} ) \, . \end{align}
Define
and note that
 \begin{equation} \int _{U'_{\!\!\gamma}} f^\sigma (r(\textbf{x}))\,d\textbf{x} = \sum _{\textbf{x} \in \mathcal{S}_{\sigma,\delta }} \delta ^{dk} f^\sigma (\textbf{x}). \end{equation}
\begin{equation} \int _{U'_{\!\!\gamma}} f^\sigma (r(\textbf{x}))\,d\textbf{x} = \sum _{\textbf{x} \in \mathcal{S}_{\sigma,\delta }} \delta ^{dk} f^\sigma (\textbf{x}). \end{equation}
Using the bound
![]() $|f^\sigma | \leqslant{e^{Bk^2}}$
gives
$|f^\sigma | \leqslant{e^{Bk^2}}$
gives
 \begin{equation} \left | \int _{U_\gamma } f^{\sigma }(r(\textbf{x}))\,d\textbf{x} - \int _{U'_{\!\!\gamma}} f^{\sigma }(r(\textbf{x}))\,d\textbf{x} \right | \leqslant{e^{Bk^2}} |U'_{\!\!\gamma} \triangle U_\gamma | \, . \end{equation}
\begin{equation} \left | \int _{U_\gamma } f^{\sigma }(r(\textbf{x}))\,d\textbf{x} - \int _{U'_{\!\!\gamma}} f^{\sigma }(r(\textbf{x}))\,d\textbf{x} \right | \leqslant{e^{Bk^2}} |U'_{\!\!\gamma} \triangle U_\gamma | \, . \end{equation}
Combining lines (20), (21) and (22), it suffices to show that
![]() $|U'_{\!\!\gamma} \triangle U_\gamma |=O\!\left (|E(G)| \delta |S| (2R)^{d(k-1)} \right )$
to complete the lemma. To this end note that
$|U'_{\!\!\gamma} \triangle U_\gamma |=O\!\left (|E(G)| \delta |S| (2R)^{d(k-1)} \right )$
to complete the lemma. To this end note that
If
![]() $\textbf{y}\in \partial U_\gamma$
, then
$\textbf{y}\in \partial U_\gamma$
, then
![]() $y_a-y_b\in \partial \Delta _{\sigma (\{a,b\})}^{(\gamma )}$
for some
$y_a-y_b\in \partial \Delta _{\sigma (\{a,b\})}^{(\gamma )}$
for some
![]() $\{a,b\}\in E(G)$
. Thus, if
$\{a,b\}\in E(G)$
. Thus, if
![]() $\textbf{x} \in X_\gamma$
, then
$\textbf{x} \in X_\gamma$
, then
for some
![]() $\{a,b\}\in E(G)$
. Arguing as in Lemma 2.6, it suffices to show that for
$\{a,b\}\in E(G)$
. Arguing as in Lemma 2.6, it suffices to show that for
![]() $t\in [\ell ]$
,
$t\in [\ell ]$
,
Suppose then that
![]() $d_\infty ( z, \partial \Delta _{t}^{(\gamma )} )\leqslant \delta$
. Since,
$d_\infty ( z, \partial \Delta _{t}^{(\gamma )} )\leqslant \delta$
. Since,
let us suppose first that
As in the proof of Claim 2.9, let
![]() $\|\cdot \|$
denote the norm associated to
$\|\cdot \|$
denote the norm associated to
![]() $K_t$
. Then by (23), there exists
$K_t$
. Then by (23), there exists
![]() $p, q\in \mathbb{R}^d$
such that
$p, q\in \mathbb{R}^d$
such that
![]() $z=p+q$
,
$z=p+q$
,
![]() $\|p\|=(1-\gamma ), \|q\|_\infty \leqslant \delta$
. By the triangle inequality, (17) and (19)
$\|p\|=(1-\gamma ), \|q\|_\infty \leqslant \delta$
. By the triangle inequality, (17) and (19)
Similarly
![]() $ \|z\|\gt 1-2\gamma$
. In other words,
$ \|z\|\gt 1-2\gamma$
. In other words,
If instead
![]() $d_\infty (z, \partial ( (1+\gamma )K_{t-1}) )\leqslant \delta$
, then by a similar argument we have that
$d_\infty (z, \partial ( (1+\gamma )K_{t-1}) )\leqslant \delta$
, then by a similar argument we have that
![]() $z\in (1+2\gamma )K_{t-1} \backslash K_{t-1}$
. By the same calculation as in (14), we conclude that
$z\in (1+2\gamma )K_{t-1} \backslash K_{t-1}$
. By the same calculation as in (14), we conclude that
as desired.
3. Reducing cluster expansion coefficients
Here we show that one can approximate
![]() $\frac{1}{|\Lambda _n|}\log Z_{\Lambda _n}(\lambda )$
using approximations of the coefficients of the cluster expansion. A slight nuisance is that
$\frac{1}{|\Lambda _n|}\log Z_{\Lambda _n}(\lambda )$
using approximations of the coefficients of the cluster expansion. A slight nuisance is that
![]() $\lambda$
need not lie in the radius of convergence of the cluster expansion; in particular, it is known [Reference Groeneveld9, Reference Penrose24] that for a repulsive potential, the radius of convergence of the cluster expansion is at most
$\lambda$
need not lie in the radius of convergence of the cluster expansion; in particular, it is known [Reference Groeneveld9, Reference Penrose24] that for a repulsive potential, the radius of convergence of the cluster expansion is at most
![]() $1/C_\phi$
(see remark 3.7 in [Reference Nguyen and Fernández23]). To get around this issue, we will use an idea of Barvinok and precompose our function
$1/C_\phi$
(see remark 3.7 in [Reference Nguyen and Fernández23]). To get around this issue, we will use an idea of Barvinok and precompose our function
![]() $f = |\Lambda _n|^{-1}\log Z_{\Lambda _n}$
with a well-chosen polynomial map sending the unit disk into our zero-free region. This will result in a function that is analytic in the disk, and the appearance of the polynomial will end up providing only a polynomial fuzz to the efficiency of our algorithms. This approach is outlined in Barvinok’s monograph [Reference Barvinok2, pg. 22] on partition functions; we isolate and prove an abstract version of this idea here.
$f = |\Lambda _n|^{-1}\log Z_{\Lambda _n}$
with a well-chosen polynomial map sending the unit disk into our zero-free region. This will result in a function that is analytic in the disk, and the appearance of the polynomial will end up providing only a polynomial fuzz to the efficiency of our algorithms. This approach is outlined in Barvinok’s monograph [Reference Barvinok2, pg. 22] on partition functions; we isolate and prove an abstract version of this idea here.
Define
![]() $\mathcal{N}_{\gamma } \;:\!=\; \{z \in \mathbb{C} \;:\;d(z,[0,1]) \lt \gamma \}$
for all
$\mathcal{N}_{\gamma } \;:\!=\; \{z \in \mathbb{C} \;:\;d(z,[0,1]) \lt \gamma \}$
for all
![]() $\gamma \in (0,1)$
.
$\gamma \in (0,1)$
.
Theorem 3.1.
Let
![]() $\gamma \in (0,1)$
. Suppose
$\gamma \in (0,1)$
. Suppose
![]() $f$
is analytic in
$f$
is analytic in
![]() $\mathcal{N}_\gamma$
and
$\mathcal{N}_\gamma$
and
![]() $|f(z)| \leqslant 1$
for all
$|f(z)| \leqslant 1$
for all
![]() $z \in \mathcal{N}_{\gamma }$
. Then there is a constant
$z \in \mathcal{N}_{\gamma }$
. Then there is a constant
![]() $C = C_\gamma \gt 0$
depending only on
$C = C_\gamma \gt 0$
depending only on
![]() $\gamma$
so that the following holds for all
$\gamma$
so that the following holds for all
![]() $\varepsilon \in (0,1/2)$
. If one can approximate each of
$\varepsilon \in (0,1/2)$
. If one can approximate each of
![]() $f^{(j)}(0)/j!$
up to an additive error of
$f^{(j)}(0)/j!$
up to an additive error of
![]() $\varepsilon ^C$
for all
$\varepsilon ^C$
for all
![]() $j = 0,1,\ldots,C \log\!(1/\varepsilon )$
in time at most
$j = 0,1,\ldots,C \log\!(1/\varepsilon )$
in time at most
![]() $T$
, then one can approximate
$T$
, then one can approximate
![]() $f(1)$
up to an additive error of
$f(1)$
up to an additive error of
![]() $\varepsilon$
in time
$\varepsilon$
in time
![]() $ C T \log\!(1/\varepsilon ) + \log ^C(1/\varepsilon ).$
$ C T \log\!(1/\varepsilon ) + \log ^C(1/\varepsilon ).$
We let
![]() $D=\{z\in \mathbb{C} \;:\; |z|\lt 1\}$
denote the open unit disk in
$D=\{z\in \mathbb{C} \;:\; |z|\lt 1\}$
denote the open unit disk in
![]() $\mathbb{C}$
. Our first step is finding a polynomial to map
$\mathbb{C}$
. Our first step is finding a polynomial to map
![]() $\overline D$
into the region
$\overline D$
into the region
![]() $\mathcal{N}_\gamma$
so that some point in
$\mathcal{N}_\gamma$
so that some point in
![]() $D$
is mapped to
$D$
is mapped to
![]() $1$
. While there are many ways to find such a polynomial (e.g. [Reference Barvinok2, Lemma 2.2.3] gives an explicit construction) the form of the polynomial is not important for us here, and so we state the relevant properties:
$1$
. While there are many ways to find such a polynomial (e.g. [Reference Barvinok2, Lemma 2.2.3] gives an explicit construction) the form of the polynomial is not important for us here, and so we state the relevant properties:
Lemma 3.2.
For each
![]() $\gamma \gt 0$
, we may find a polynomial
$\gamma \gt 0$
, we may find a polynomial
![]() $\Phi = \Phi _\gamma$
so that
$\Phi = \Phi _\gamma$
so that
![]() $\Phi (\overline{D}) \subset \mathcal{N}_\gamma$
,
$\Phi (\overline{D}) \subset \mathcal{N}_\gamma$
,
![]() $\Phi (0) = 0$
and there is a point
$\Phi (0) = 0$
and there is a point
![]() $z_1\in D$
so that
$z_1\in D$
so that
![]() $\Phi (z_1) = 1$
.
$\Phi (z_1) = 1$
.
The point now will be to work with the function
![]() $g \;:\; \overline{D} \to \mathbb{C}$
defined by
$g \;:\; \overline{D} \to \mathbb{C}$
defined by
![]() $g = f \circ \Phi$
. Under the assumptions of Theorem 3.1, such a function
$g = f \circ \Phi$
. Under the assumptions of Theorem 3.1, such a function
![]() $g$
is analytic in
$g$
is analytic in
![]() $D$
and
$D$
and
![]() $|g(z)| \leqslant 1$
for all
$|g(z)| \leqslant 1$
for all
![]() $z \in \overline{D}$
. The Cauchy integral formula will imply that we can approximate
$z \in \overline{D}$
. The Cauchy integral formula will imply that we can approximate
![]() $g$
by its Taylor polynomial provided we are not near the boundary:
$g$
by its Taylor polynomial provided we are not near the boundary:
Fact 3.3.
Let
![]() $g$
be analytic in
$g$
be analytic in
![]() $D$
with
$D$
with
![]() $|g(z)| \leqslant 1$
for all
$|g(z)| \leqslant 1$
for all
![]() $z \in \overline{D}$
. Then for all
$z \in \overline{D}$
. Then for all
![]() $z \in D$
and
$z \in D$
and
![]() $k \in \mathbb{N}$
, we have
$k \in \mathbb{N}$
, we have
 \begin{equation*}\left |g(z) - \sum _{j = 0}^{k-1} \frac {g^{(j)}(0) }{j!} z^j \right | \leqslant \frac {|z|^{k}}{1 - |z|}.\end{equation*}
\begin{equation*}\left |g(z) - \sum _{j = 0}^{k-1} \frac {g^{(j)}(0) }{j!} z^j \right | \leqslant \frac {|z|^{k}}{1 - |z|}.\end{equation*}
Proof. Bound
 \begin{equation*}\left |g(z) - \sum _{j = 0}^{k-1} \frac {g^{(j)}(0) }{j!} z^j \right | \leqslant \sum _{j \geqslant k} \!\left |\frac {g^{(j)}(0) }{j!} \right |\cdot |z|^j\end{equation*}
\begin{equation*}\left |g(z) - \sum _{j = 0}^{k-1} \frac {g^{(j)}(0) }{j!} z^j \right | \leqslant \sum _{j \geqslant k} \!\left |\frac {g^{(j)}(0) }{j!} \right |\cdot |z|^j\end{equation*}
and note that by Cauchy’s integral formula we have
 \begin{equation*}\left |\frac {g^{(j)}(0) }{j!}\right |\leqslant 1.\end{equation*}
\begin{equation*}\left |\frac {g^{(j)}(0) }{j!}\right |\leqslant 1.\end{equation*}
Summing over
![]() $j \geqslant k$
completes the proof.
$j \geqslant k$
completes the proof.
Let
![]() $z_1$
be as in Lemma 3.2. It follows that in order to approximate
$z_1$
be as in Lemma 3.2. It follows that in order to approximate
![]() $f(1) = g(z_1)$
up to an additive error of
$f(1) = g(z_1)$
up to an additive error of
![]() $\varepsilon$
, it is sufficient to approximate the first
$\varepsilon$
, it is sufficient to approximate the first
![]() $k = C_\gamma \log\!(1/\varepsilon )$
terms
$k = C_\gamma \log\!(1/\varepsilon )$
terms
![]() $g^{(j)}(0)/j!$
up to an error of
$g^{(j)}(0)/j!$
up to an error of
![]() $\varepsilon/(2k)$
each. To do so, we will relate the derivatives of
$\varepsilon/(2k)$
each. To do so, we will relate the derivatives of
![]() $g$
to those of
$g$
to those of
![]() $f$
. Iterating the chain rule gives the classical Faà di Bruno formula:
$f$
. Iterating the chain rule gives the classical Faà di Bruno formula:
Fact 3.4 (Faà di Bruno’s formula). Let
![]() $\Phi$
and
$\Phi$
and
![]() $f$
be analytic at
$f$
be analytic at
![]() $0$
with
$0$
with
![]() $\Phi (0) = 0$
and set
$\Phi (0) = 0$
and set
![]() $g = f\circ \Phi$
. Then for each
$g = f\circ \Phi$
. Then for each
![]() $n \in \mathbb{N}$
, we have
$n \in \mathbb{N}$
, we have
where
![]() $B_{n,k}(x_1,x_2,\ldots,x_{n-k+1})$
are the Bell polynomials given by
$B_{n,k}(x_1,x_2,\ldots,x_{n-k+1})$
are the Bell polynomials given by
where the sum is over all sequences of non-negative integers
![]() $j_1,j_2,\ldots,j_{n - k +1}$
satisfying
$j_1,j_2,\ldots,j_{n - k +1}$
satisfying
![]() $\sum j_i = k$
and
$\sum j_i = k$
and
![]() $\sum i j_i = n$
.
$\sum i j_i = n$
.
To make use of this fact, we will need to evaluate the Bell polynomials
![]() $B_{n,k}$
at derivatives of our polynomial
$B_{n,k}$
at derivatives of our polynomial
![]() $\Phi$
. A simple term-by-term bound will be good enough for our purposes.
$\Phi$
. A simple term-by-term bound will be good enough for our purposes.
Lemma 3.5.
For each polynomial
![]() $\Phi$
, there is a constant
$\Phi$
, there is a constant
![]() $C = C_\Phi \gt 0$
so that the following holds. For all
$C = C_\Phi \gt 0$
so that the following holds. For all
![]() $n, k \in \mathbb{N}$
, we may compute
$n, k \in \mathbb{N}$
, we may compute
![]() $B_{n,k}(\Phi '(0),\Phi ''(0),\ldots,\Phi ^{(n-k+1)}(0))$
in time
$B_{n,k}(\Phi '(0),\Phi ''(0),\ldots,\Phi ^{(n-k+1)}(0))$
in time
![]() $O(k^{C})$
and we have the bound
$O(k^{C})$
and we have the bound
Proof. First compute all derivatives of
![]() $\Phi$
at
$\Phi$
at
![]() $0$
, which takes
$0$
, which takes
![]() $O_\Phi (1)$
time since
$O_\Phi (1)$
time since
![]() $\Phi$
is a polynomial. Set
$\Phi$
is a polynomial. Set
![]() $x_j = \Phi ^{(j)}(0)$
and note that
$x_j = \Phi ^{(j)}(0)$
and note that
![]() $x_j = 0$
for
$x_j = 0$
for
![]() $j \gt d$
where
$j \gt d$
where
![]() $d$
is the degree of
$d$
is the degree of
![]() $\Phi$
. We may thus reduce the sum in (25) to those for which
$\Phi$
. We may thus reduce the sum in (25) to those for which
![]() $j_i = 0$
for all
$j_i = 0$
for all
![]() $i \gt d$
as all other summands are
$i \gt d$
as all other summands are
![]() $0$
. Since the values
$0$
. Since the values
![]() $j_1,\ldots,j_d$
are non-negative integers of size at most
$j_1,\ldots,j_d$
are non-negative integers of size at most
![]() $k$
, we have
$k$
, we have
![]() $(k+1)^d$
choices for the sequence
$(k+1)^d$
choices for the sequence
![]() $(j_1,\ldots,j_d)$
. Moreover, the constraints
$(j_1,\ldots,j_d)$
. Moreover, the constraints
![]() $\sum j_i = k$
and
$\sum j_i = k$
and
![]() $\sum i j_i = n$
imply that
$\sum i j_i = n$
imply that
![]() $n\leqslant dk$
and so each summand in (25) can be computed in time
$n\leqslant dk$
and so each summand in (25) can be computed in time
![]() $O_d(k^{C^{\prime}})$
for some
$O_d(k^{C^{\prime}})$
for some
![]() $C'=C'_{\!\!d}\gt 0$
. We may, therefore, calculate the sum (25) in time
$C'=C'_{\!\!d}\gt 0$
. We may, therefore, calculate the sum (25) in time
![]() $O_\Phi (k^C)$
for some
$O_\Phi (k^C)$
for some
![]() $C=C_d\gt 0$
.
$C=C_d\gt 0$
.
To see the claimed bound, apply the triangle inequality to see
Relaxing the sum to consist of sequences satisfying
![]() $\sum j_i = k$
, the binomial theorem gives
$\sum j_i = k$
, the binomial theorem gives
for
![]() $C$
large enough with respect to
$C$
large enough with respect to
![]() $\Phi$
.
$\Phi$
.
The proof of Theorem 3.1 now follows from some bookkeeping.
Proof of Theorem
3.1. Apply Lemma 3.2 to find a polynomial
![]() $\Phi =\Phi _\gamma$
satisfying the hypotheses of the lemma and define
$\Phi =\Phi _\gamma$
satisfying the hypotheses of the lemma and define
![]() $g = f \circ \Phi$
. Then by Fact 3.3 we may take
$g = f \circ \Phi$
. Then by Fact 3.3 we may take
![]() $k \;:\!=\; C_\gamma \log\!(1/\varepsilon )$
large enough so that
$k \;:\!=\; C_\gamma \log\!(1/\varepsilon )$
large enough so that
 \begin{equation*}\left |g(z_1) - \sum _{j = 0}^{k-1}\frac {g^{(j)}(0)}{j!} z_1^j \right | \leqslant \varepsilon/2.\end{equation*}
\begin{equation*}\left |g(z_1) - \sum _{j = 0}^{k-1}\frac {g^{(j)}(0)}{j!} z_1^j \right | \leqslant \varepsilon/2.\end{equation*}
Since
![]() $g(z_1) = f(1)$
, it is thus sufficient to approximate
$g(z_1) = f(1)$
, it is thus sufficient to approximate
![]() $g^{(j)}(0)/j!$
for
$g^{(j)}(0)/j!$
for
![]() $j = 0,1,\ldots,k-1$
up to an additive error of at most
$j = 0,1,\ldots,k-1$
up to an additive error of at most
![]() $\delta \;:\!=\; \varepsilon/(2k)$
. By Fact 3.4 and Lemma 3.5 we may expand
$\delta \;:\!=\; \varepsilon/(2k)$
. By Fact 3.4 and Lemma 3.5 we may expand
 \begin{equation*}\frac {g^{(j)}}{j!}(0) = \sum _{i = 1}^j \frac {f^{(i)}(0)}{i!} B_{i,j}\end{equation*}
\begin{equation*}\frac {g^{(j)}}{j!}(0) = \sum _{i = 1}^j \frac {f^{(i)}(0)}{i!} B_{i,j}\end{equation*}
where the coefficients
![]() $B_{i,j}$
satisfy
$B_{i,j}$
satisfy
![]() $|B_{i,j}| \leqslant e^{C i} \leqslant e^{C k} = O(\varepsilon ^{-C})$
and may be computed in time
$|B_{i,j}| \leqslant e^{C i} \leqslant e^{C k} = O(\varepsilon ^{-C})$
and may be computed in time
![]() $O(k^C) = O(\log ^C(1/\varepsilon ))$
. Thus, if we take
$O(k^C) = O(\log ^C(1/\varepsilon ))$
. Thus, if we take
![]() $C'$
large enough (as a function of
$C'$
large enough (as a function of
![]() $\gamma$
) and approximate
$\gamma$
) and approximate
![]() $f^{(i)}(0)/i!$
up to additive error
$f^{(i)}(0)/i!$
up to additive error
![]() $\varepsilon ^{C'}$
, we obtain an approximation to
$\varepsilon ^{C'}$
, we obtain an approximation to
![]() $g(z_1) = f(1)$
up to additive error
$g(z_1) = f(1)$
up to additive error
![]() $\varepsilon$
.
$\varepsilon$
.
4. Proof of Theorem 1.3
Proof of Theorem
1.3. Set
![]() $f(z)\;:\!=\; \frac{1}{C|\Lambda _n|} \log Z_{\Lambda _n}(\lambda z)$
, where
$f(z)\;:\!=\; \frac{1}{C|\Lambda _n|} \log Z_{\Lambda _n}(\lambda z)$
, where
![]() $C$
is as in Assumption 1.2. Then
$C$
is as in Assumption 1.2. Then
![]() $f$
satisfies the hypotheses of Theorem 3.1, and note that by (11) we have
$f$
satisfies the hypotheses of Theorem 3.1, and note that by (11) we have
![]() $f^{(j)}(0)= \lambda ^j C_j(\Lambda _n)/(C |\Lambda _n|)$
. If we set
$f^{(j)}(0)= \lambda ^j C_j(\Lambda _n)/(C |\Lambda _n|)$
. If we set
![]() $\delta = \varepsilon/(C |\Lambda _n|)$
, then we are seeking to approximate
$\delta = \varepsilon/(C |\Lambda _n|)$
, then we are seeking to approximate
![]() $f(1)$
up to an additive error of
$f(1)$
up to an additive error of
![]() $\delta$
. By Propostion 2.1, for each
$\delta$
. By Propostion 2.1, for each
![]() $j = 0,1,\ldots, O(\log\!(1/\delta ) )$
, we may compute
$j = 0,1,\ldots, O(\log\!(1/\delta ) )$
, we may compute
![]() $f^{(j)}(0)$
up to additive error
$f^{(j)}(0)$
up to additive error
![]() $\delta ^{O(1)}$
in time at most
$\delta ^{O(1)}$
in time at most
![]() $O(|\Lambda _n| \delta ^{-O(j)}e ^{O(j^3)}) = \exp\!(O(\log ^3(1/\delta ))).$
Applying Theorem 3.1 completes the proof.
$O(|\Lambda _n| \delta ^{-O(j)}e ^{O(j^3)}) = \exp\!(O(\log ^3(1/\delta ))).$
Applying Theorem 3.1 completes the proof.
Acknowledgements
MJ is supported by a UKRI Future Leaders Fellowship MR/W007320/1. MM is supported in part by NSF grant DMS-2137623. MR gratefully acknowledges support from the Bogazici Solidarity Fund and the Institute of Mathematical Sciences, Chennai, where part of this work was carried out. We would like to thank Will Perkins for helpful discussions. We also thank the anonymous referee for their careful reading and helpful comments.