Article contents
The multiple number field sieve for medium- and high-characteristic finite fields
Published online by Cambridge University Press: 01 August 2014
Abstract
In this paper we study the discrete logarithm problem in medium- and high-characteristic finite fields. We propose a variant of the number field sieve (NFS) based on numerous number fields. Our improved algorithm computes discrete logarithms in 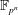 $\def \xmlpi #1{}\def \mathsfbi #1{\boldsymbol {\mathsf {#1}}}\let \le =\leqslant \let \leq =\leqslant \let \ge =\geqslant \let \geq =\geqslant \def \Pr {\mathit {Pr}}\def \Fr {\mathit {Fr}}\def \Rey {\mathit {Re}}\mathbb{F}_{p^n}$ for the whole range of applicability of the NFS and lowers the asymptotic complexity from
$\def \xmlpi #1{}\def \mathsfbi #1{\boldsymbol {\mathsf {#1}}}\let \le =\leqslant \let \leq =\leqslant \let \ge =\geqslant \let \geq =\geqslant \def \Pr {\mathit {Pr}}\def \Fr {\mathit {Fr}}\def \Rey {\mathit {Re}}\mathbb{F}_{p^n}$ for the whole range of applicability of the NFS and lowers the asymptotic complexity from 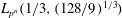 $L_{p^n}({1/3},({128/9})^{1/3})$ to
$L_{p^n}({1/3},({128/9})^{1/3})$ to 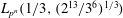 $L_{p^n}({1/3},(2^{13}/3^6)^{1/3})$ in the medium-characteristic case, and from
$L_{p^n}({1/3},(2^{13}/3^6)^{1/3})$ in the medium-characteristic case, and from 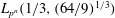 $L_{p^n}({1/3},({64/9})^{1/3})$ to
$L_{p^n}({1/3},({64/9})^{1/3})$ to 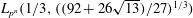 $L_{p^n}({1/3},((92 + 26 \sqrt{13})/27)^{1/3})$ in the high-characteristic case.
$L_{p^n}({1/3},((92 + 26 \sqrt{13})/27)^{1/3})$ in the high-characteristic case.
MSC classification
- Type
- Research Article
- Information
- LMS Journal of Computation and Mathematics , Volume 17 , Special Issue A: Algorithmic Number Theory Symposium XI , 2014 , pp. 230 - 246
- Copyright
- © The Author(s) 2014
References
- 16
- Cited by


