Crossref Citations
This article has been cited by the following publications. This list is generated based on data provided by
Crossref.
Junnila, Ville
Laihonen, Tero
and
Parreau, Aline
2013.
Tolerant identification with Euclidean balls.
Networks,
Vol. 61,
Issue. 3,
p.
212.
Ghebleh, M.
and
Niepel, L.
2013.
Locating and identifying codes in circulant networks.
Discrete Applied Mathematics,
Vol. 161,
Issue. 13-14,
p.
2001.
Foucaud, Florent
2013.
Combinatorial Algorithms.
Vol. 8288,
Issue. ,
p.
150.
Mitsche, Dieter
and
Rué, Juanjo
2015.
On the limiting distribution of the metric dimension for random forests.
European Journal of Combinatorics,
Vol. 49,
Issue. ,
p.
68.
Foucaud, Florent
2015.
Decision and approximation complexity for identifying codes and locating-dominating sets in restricted graph classes.
Journal of Discrete Algorithms,
Vol. 31,
Issue. ,
p.
48.
Bazgan, Cristina
Foucaud, Florent
and
Sikora, Florian
2016.
Combinatorial Optimization and Applications.
Vol. 10043,
Issue. ,
p.
92.
Foucaud, Florent
Mertzios, George B.
Naserasr, Reza
Parreau, Aline
and
Valicov, Petru
2016.
Graph-Theoretic Concepts in Computer Science.
Vol. 9224,
Issue. ,
p.
456.
Foucaud, Florent
Mertzios, George B.
Naserasr, Reza
Parreau, Aline
and
Valicov, Petru
2017.
Identification, Location-Domination and Metric Dimension on Interval and Permutation Graphs. II. Algorithms and Complexity.
Algorithmica,
Vol. 78,
Issue. 3,
p.
914.
Foucaud, Florent
Mertzios, George B.
Naserasr, Reza
Parreau, Aline
and
Valicov, Petru
2017.
Identification, location–domination and metric dimension on interval and permutation graphs. I. Bounds.
Theoretical Computer Science,
Vol. 668,
Issue. ,
p.
43.
Givens, Robin M.
Kincaid, Rex K.
Mao, Weizhen
and
Yu, Gexin
2018.
An integer linear program for mixed-weight open locating-dominating sets.
p.
1.
Gledel, Valentin
and
Parreau, Aline
2019.
Identification of points using disks.
Discrete Mathematics,
Vol. 342,
Issue. 1,
p.
256.
Bazgan, Cristina
Foucaud, Florent
and
Sikora, Florian
2019.
Parameterized and approximation complexity of Partial VC Dimension.
Theoretical Computer Science,
Vol. 766,
Issue. ,
p.
1.
Argiroffo, G.
Bianchi, S.
Lucarini, Y.
and
Wagler, A.
2019.
The Identifying Code, the Locating-dominating, the Open Locating-dominating and the Locating Total-dominating Problems Under Some Graph Operations.
Electronic Notes in Theoretical Computer Science,
Vol. 346,
Issue. ,
p.
135.
Argiroffo, Gabriela R.
Bianchi, Silvia M.
Lucarini, Yanina
and
Wagler, Annegret K.
2020.
Linear-time algorithms for three domination-based separation problems in block graphs.
Discrete Applied Mathematics,
Vol. 281,
Issue. ,
p.
6.
Song, Shu Jiao
Zhang, Weiqian
Xu, Can
and
Ali, Akbar
2021.
Locating and Identifying Codes in Circulant Graphs.
Discrete Dynamics in Nature and Society,
Vol. 2021,
Issue. ,
p.
1.
Angel, D.
Arputhamary, I. Annammal
and
Ezhilarasi, K.
2021.
Location Domination for Generalized Friendship Graphs Analytics.
p.
865.
Argiroffo, Gabriela
Bianchi, Silvia
Lucarini, Yanina
and
Wagler, Annegret
2022.
Polyhedra associated with locating-dominating, open locating-dominating and locating total-dominating sets in graphs.
Discrete Applied Mathematics,
Vol. 322,
Issue. ,
p.
465.
Angel, D.
Arputhamary, I. Annammal
Revathi, R.
and
Raja, A.
2022.
Location dominating sets in friendship graphs.
Vol. 2516,
Issue. ,
p.
210058.
Dey, Sanjana
Foucaud, Florent
Nandy, Subhas C.
and
Sen, Arunabha
2023.
Complexity and Approximation for Discriminating and Identifying Code Problems in Geometric Setups.
Algorithmica,
Vol. 85,
Issue. 7,
p.
1850.
Bianchi, Silvia M.
Chakraborty, Dipayan
Lucarini, Yanina
and
Wagler, Annegret K.
2024.
Algorithms and Discrete Applied Mathematics.
Vol. 14508,
Issue. ,
p.
255.
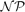 -complete even for bipartite graphs. First, we improve this result by showing that the problem remains
-complete even for bipartite graphs. First, we improve this result by showing that the problem remains 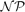 -complete for bipartite planar unit disk graphs. Then, we address the question of the existence of an identifying code for random unit disk graphs. We derive the probability that there exists an identifying code as a function of the radius of the disks, and we find that for all interesting ranges of r this probability is bounded away from one. The results obtained are in sharp contrast to those concerning random graphs in the Erdős–Rényi model. Another well-studied class of codes is that of locating–dominating codes, which are less demanding than identifying codes. A locating–dominating code always exists, but minimizing its size is still
-complete for bipartite planar unit disk graphs. Then, we address the question of the existence of an identifying code for random unit disk graphs. We derive the probability that there exists an identifying code as a function of the radius of the disks, and we find that for all interesting ranges of r this probability is bounded away from one. The results obtained are in sharp contrast to those concerning random graphs in the Erdős–Rényi model. Another well-studied class of codes is that of locating–dominating codes, which are less demanding than identifying codes. A locating–dominating code always exists, but minimizing its size is still 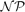 -complete in general. We extend this result to our setting by showing that this question remains
-complete in general. We extend this result to our setting by showing that this question remains 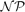 -complete for arbitrary planar unit disk graphs. Finally, we study the minimum size of such a code in random unit disk graphs, and we prove that with probability tending to one, it is of size (n/r)2/3+o(1) if r ≤
-complete for arbitrary planar unit disk graphs. Finally, we study the minimum size of such a code in random unit disk graphs, and we prove that with probability tending to one, it is of size (n/r)2/3+o(1) if r ≤ 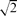 /2−ϵ is chosen such that nr2 → ∞, and of size n1+o(1) if nr2 ≪ lnn.
/2−ϵ is chosen such that nr2 → ∞, and of size n1+o(1) if nr2 ≪ lnn.

